A Guide to Voice Biometrics Authentication
Passwords are a pain. We forget them, we lose them, and they get stolen all the time. But what if your password was something you could never lose because it's literally a part of you? That's the simple, powerful idea behind voice biometrics authentication.
It’s a security method that uses the one-of-a-kind characteristics of your voice to prove you are who you say you are. Think of it less like a password and more like a vocal fingerprint. It's not about what you say, but who is doing the saying.
Your Voice Is the Ultimate Password

Imagine a key that’s so unique it's woven into your very biology. That's voice biometrics in a nutshell. It turns the distinct patterns of your speech into a secure key for access. Unlike a password that can be phished or a keycard that can be swiped, your voice is an identifier that’s incredibly difficult to fake.
This isn’t science fiction. It’s the result of blending biology and technology together. Your voice is shaped by more than 100 different physical and behavioral traits. When you speak, these all combine to create a "voiceprint" that is as unique to you as your actual fingerprint.
What Makes a Voiceprint Unique
The system isn't just listening to your words; it’s analyzing the deep mechanics of your speech. It breaks down your voice into two distinct categories of traits.
- Physiological Traits: These are all about your physical anatomy—the size and shape of your vocal tract, your larynx, even your nasal passages. These are the physical characteristics that are almost impossible for an imposter to replicate.
- Behavioral Traits: This is the stuff you’ve learned over a lifetime. It includes your personal rhythm, the cadence and pitch of your speech, and how quickly you talk. These habits are deeply ingrained and hard to mimic convincingly.
It’s easy to mix up voice recognition and voice biometrics. Voice recognition, like what Siri or Alexa uses, figures out what you’re saying. Voice biometrics authentication confirms who is saying it.
Two Core Methods of Authentication
Voice biometrics typically works in one of two ways, and each one is suited for different situations. Getting a handle on these two approaches is the key to seeing just how flexible this technology can be.
First, you have text-dependent authentication. This is the more direct method. The system prompts you to say a specific phrase, something like "My voice is my password." Because the system already knows what words to expect, it can pour all its energy into analyzing the biometric markers in your voice and matching them to your stored voiceprint. It’s a very active, deliberate step.
The other approach is text-independent authentication. This one is much more passive. It analyzes your voice during a normal conversation, like when you're on the phone with a customer service agent. You don't have to say a specific passphrase; the system just figures out who you are in the background. This creates a really smooth, friction-free experience where security feels totally invisible.
Both methods offer a strong defense against fraud because they shift the focus from what you know (a password) to who you are. This fundamental change is completely reshaping how we think about digital identity.
How Voice Biometric Technology Actually Works
To really get a handle on voice biometrics authentication, you need to pop the hood and see what’s running inside. The whole process is a fascinating mix of biology, advanced math, and artificial intelligence, all working together to turn your voice into a digital key. It all boils down to two main stages: first, you enroll to create your "voiceprint," and then you verify your identity using it.
Think of the enrollment part like getting a key cut for a new lock. The system asks you to say a few things, which gives it a baseline sample of your voice. This first step is absolutely critical because it’s where the system gathers all the raw material it needs to build your unique, secure profile.
But it's not just recording words. The system uses sophisticated algorithms to dissect the sound of your voice, pulling out more than 100 different vocal characteristics. These aren't just about what you say, but how you say it—things like the physical shape of your vocal tract (physiology) and your personal rhythm and pacing (behavior).
This collection of data points is then converted into a heavily encrypted digital file we call a voiceprint. Crucially, this is a mathematical representation of your voice, not an audio recording. That’s a key distinction for privacy; you can't reverse-engineer a voiceprint to playback someone's actual voice.
Creating a Secure Voiceprint
Once the system has your voice samples, the real magic starts. AI algorithms get to work, poring over the unique frequencies, pitches, and cadences that make your voice yours and yours alone.
This analysis is what generates the voiceprint, which is essentially a secure template stored for all future comparisons. The whole point is to capture the core, stable elements of your speech. This makes the system incredibly resilient to temporary changes, like when you have a cold or a sore throat. It’s focused on the underlying structure of your voice, not the surface-level sound.
This infographic breaks down the journey from speaking a phrase to getting verified.
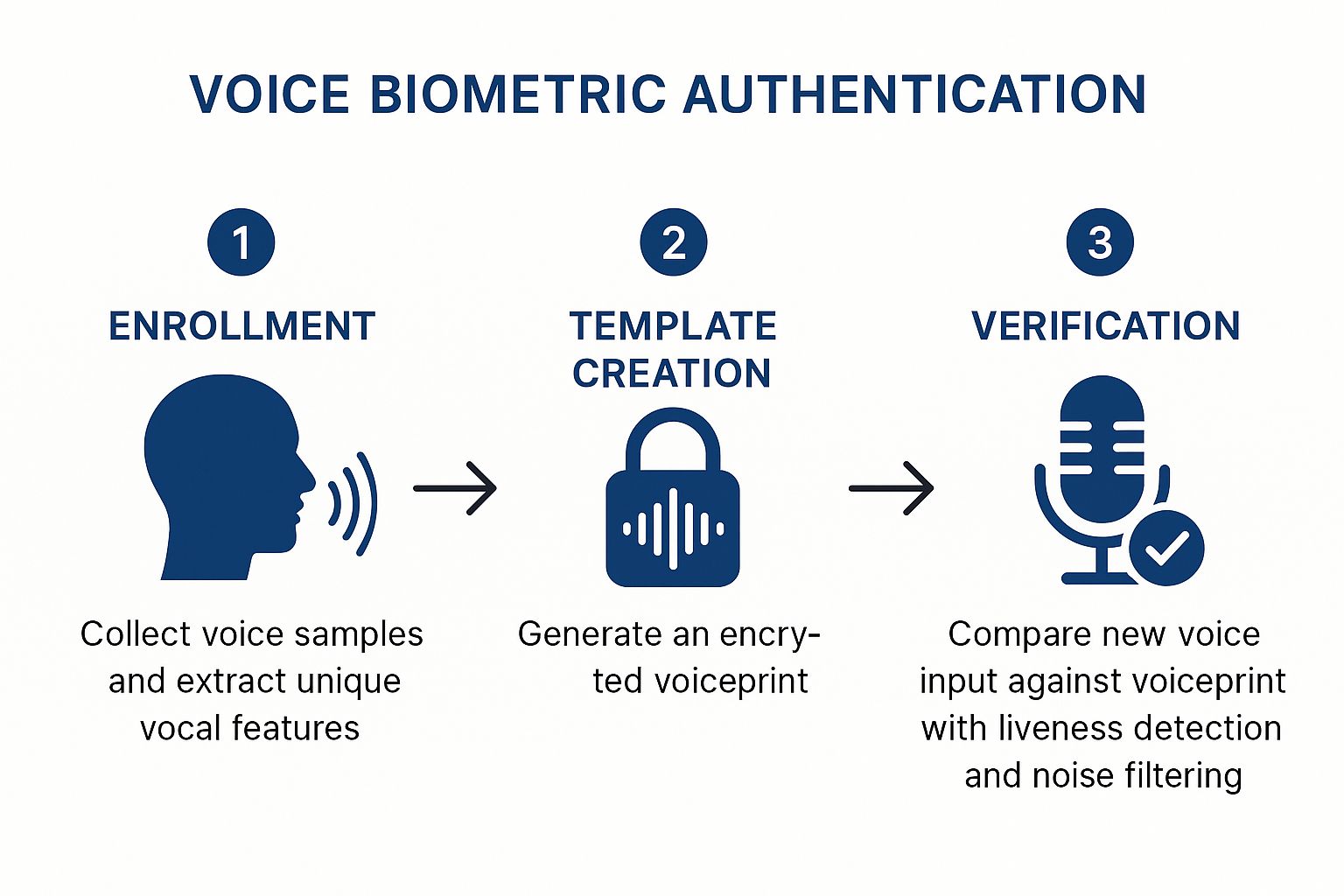
As you can see, the flow is pretty straightforward: gather voice samples, extract the unique features, create that encrypted voiceprint, and then use it to verify you later on.
The Verification Phase: Unlocking Access
After your voiceprint is securely filed away, the verification phase is where the tech shows its true value. This is the moment of truth when the system has to figure out, "Is this person really who they say they are?" The process is quick, seamless, and impressively smart.
When you try to log in or approve a transaction, you'll be prompted to speak again. The system captures this new audio on the fly and runs the exact same deep analysis it did during enrollment, creating a temporary voiceprint just for this one-time comparison.
This new sample is then squared up against your stored template, and the system’s algorithms calculate a similarity score. If that score is high enough to pass a pre-set confidence threshold, you're in. If it doesn't match, access is denied, stopping a potential intruder in their tracks.
At its heart, verification is a sophisticated matching game. The system is essentially asking, "How closely does this live voice match the unique mathematical model we have on file?" A high score means a confident match, while a low score signals a potential imposter.
Modern voice biometrics authentication systems also come armed with extra layers of security to stay ahead of fraudsters.
- Liveness Detection: This is a clever feature designed to sniff out recordings. The AI looks for tiny acoustic patterns and micro-variations that only exist in live human speech, making it easy to tell a real person from a playback.
- Noise Filtering: We're not always in a quiet room. Whether you’re at a bustling coffee shop or a noisy office, the AI is smart enough to isolate your voice from all that background chatter, ensuring it can still get an accurate reading.
- Adaptability: The system is also designed to learn and adapt. It can recognize your core voiceprint even if your pitch changes slightly because you're sick or stressed, which helps avoid those frustrating false rejections.
This entire process is quite similar to how modern voice-to-text AI systems filter out background noise to produce cleaner transcriptions. By combining feature extraction, template matching, and AI-powered security checks, your voice becomes a surprisingly powerful and reliable key.
Why Voice Authentication Is a Game-Changer for Modern Security

For years, we've relied on a shaky foundation for digital security: passwords and PINs. It’s a system we all know is broken. We're forced to create complex secrets that are hard to remember but surprisingly easy for criminals to steal, guess, or phish. This leads to a constant tug-of-war between security and convenience, where stronger passwords just mean more forgotten logins and weaker ones are an open invitation for fraud.
This core weakness has pushed businesses and their customers to look for something better. We need authentication that is not just stronger, but also doesn't feel like a chore. Voice biometrics authentication is the answer. It completely changes the game by verifying you based on who you are, not what you know.
Think about it—your voice is uniquely yours. It’s a deeply personal identifier that acts as a powerful key. Using it for security builds a strong defense against common attacks like credential stuffing and social engineering, all while getting rid of the hassle of typing things in.
A Rare Win-Win: Tighter Security, Smoother Experience
The real magic of voice biometrics is that it solves two problems at once. It boosts security and makes life easier for the user, a combination that’s incredibly rare in identity verification. This dual advantage is exactly why it's catching on so fast across so many industries.
From a security standpoint, it’s a massive upgrade. Faking a unique voiceprint is exponentially harder than swiping a password from a database. At the same time, it creates a completely natural and seamless experience. Instead of fumbling with a keyboard to enter a long password, a user can just say a few words to prove it’s really them.
This kind of speed and simplicity is a lifesaver in places like busy call centers or mobile banking apps, where every second counts. Voice biometrics turns what used to be a clunky security hurdle into an invisible, fluid part of the conversation.
Keeping Pace With a Demanding World
So, what's driving this big shift? A few key trends have created the perfect environment for voice biometrics authentication to take off. We're seeing more sophisticated fraud, customers are demanding faster and easier service, and voice-activated devices are everywhere. It’s becoming clear that old-school security just can't keep up anymore.
The market numbers tell the whole story. The global voice biometrics market is already valued at around USD 2.30 billion and is expected to explode to USD 15.69 billion by 2032. That's a compound annual growth rate of about 27.5%, signaling a clear and decisive move away from outdated security methods.
But this growth isn't just about blocking threats; it's about creating better, safer interactions for everyone. Voice biometrics is a fantastic addition to a multi-layered defense, often used as a form of two-factor authentication. It also aligns perfectly with modern security models like Zero Trust, which operates on the principle of "never trust, always verify." If you're curious about this concept, we break it down in our guide on Zero Trust security: https://www.whisperit.ai/blog/what-is-zero-trust-security.
Ultimately, voice biometrics isn't just a futuristic idea—it's a practical and powerful solution for the security challenges we're facing right now.
Comparing Active and Passive Voice Biometrics
When you decide to use voice biometrics for authentication, one of the first and most important calls you'll make is choosing between an active or a passive approach. They both get the job done, but how they do it completely changes the user experience and where they fit best.
To put it simply, think of it like this: active verification is like being asked to show your ID at a security desk. It's a very clear, deliberate action. Passive verification, on the other hand, is like a security guard who recognizes you by sight as you walk past, without you ever breaking stride.
One creates a visible security checkpoint, while the other weaves security invisibly into the background. Your choice really boils down to what you're trying to accomplish.
Active Voice Biometrics: The Deliberate Checkpoint
Active voice biometrics, often called text-dependent verification, is the straightforward approach. It asks the user to do something specific to prove who they are. This usually means speaking a set passphrase, like, "My voice is my password," or repeating a short string of randomly generated numbers.
This method is explicit. The user is fully aware they're going through a security check. Because the system knows exactly which words to listen for, it can focus all its resources on matching the unique characteristics of that person's voice to their stored voiceprint.
This makes it an excellent choice for high-stakes interactions where you need a clear, intentional verification step. It also creates an undeniable audit trail, proving the user actively consented to the security check.
- Great for: Logging into a mobile banking app, authorizing a large money transfer, or resetting a forgotten password.
- The Experience: The user is an active participant, making the security process feel tangible and secure.
- Security Focus: Designed for high accuracy in those single, critical moments of verification.
Passive Voice Biometrics: The Invisible Guardian
On the flip side, we have passive voice biometrics, also known as text-independent verification. This one works its magic completely behind the scenes. It analyzes a person's voice during a normal conversation without ever asking them to say a specific phrase.
Imagine a customer calling your support center. A passive system can analyze the first 15-30 seconds of their natural speech as they explain their issue. By the time the agent is ready to help, the customer has already been authenticated—without even realizing it.
This creates a wonderfully smooth experience. It not only speeds up service but also gives you the power to continuously monitor the call for potential fraud if a different voice suddenly appears on the line.
This approach is all about delivering robust, ongoing authentication without getting in the user's way. It's security that improves the experience instead of slowing it down. The best systems can tap into the broader advantages of voice recognition software to make this process even more effective.
The seamless nature of passive biometrics is a game-changer for customer-focused industries where speed and convenience are everything. No more frustrating security questions—just quick, helpful service.
At a Glance: Comparing the Two Approaches
To help you visualize the difference, let's put these two methods side-by-side. Seeing their core features compared directly can make it much clearer which one is the right fit for your specific needs.
| Feature | Active Voice Biometrics | Passive Voice Biometrics |
|---|---|---|
| User Interaction | User must speak a specific phrase. | Analyzes natural, free-form speech. |
| User Awareness | High (user knows they are being verified). | Low (verification is invisible). |
| Experience | Deliberate and explicit. | Seamless and frictionless. |
| Typical Use Cases | Secure logins, password resets, transaction approvals. | Call center authentication, fraud detection. |
| Data Requirement | Needs a short, specific utterance. | Needs a few seconds of natural conversation. |
| Primary Goal | One-time, high-security gatekeeping. | Continuous, background verification. |
Ultimately, both active and passive voice biometrics offer powerful security. The key is to match the method to the moment—choosing the explicit checkpoint when it's needed and the invisible guardian when the user experience is paramount.
Real-World Use Cases for Voice Biometrics

The theory behind voice biometrics authentication is one thing, but where it really comes alive is in solving real, everyday problems. Across different industries, this technology is quickly moving from a novel concept to a go-to tool for tightening security and making customer interactions feel effortless. It’s not just about locking things down; it’s about making access both safer and simpler.
Let’s look at how a few sectors are putting voice biometrics to work. From high-stakes financial trades to routine customer service calls, you'll see just how versatile it can be.
Fortifying Banking and Financial Services
Nowhere is the impact of voice biometrics more obvious than in the financial world. With billions of dollars on the line, banks and fintechs are in a constant battle against fraud, especially account takeover schemes that target their call centers. Voice biometrics gives them a powerful, almost invisible, shield.
Imagine a customer calling their bank. From the moment they say "hello," a passive voice biometrics system can start confirming it's really them. This completely sidesteps those clunky security questions while flagging a potential fraudster's voice in real time.
Here are a couple of common scenarios:
- Securing Phone Banking: Forget trying to remember your mother's maiden name. The system verifies who you are through the natural flow of conversation, which slashes call times and makes the whole process more secure.
- Authorizing High-Value Transactions: For something as critical as a large wire transfer, the system can ask the user to speak a specific passphrase. This adds a solid layer of confirmation right when it's needed most.
A major UK bank saw a stunning 93% reduction in account takeover fraud at its call centers after bringing in passive voice biometrics. That’s an immediate, game-changing impact.
This tech turns call centers from a common weak point into a fortress, protecting the bank and its customers all at once.
Protecting Sensitive Healthcare Data
In healthcare, the stakes for data security are just as high. Patient privacy is non-negotiable, yet doctors and patients need fast, secure access to medical records. It’s no surprise that voice biometrics adoption is surging in the US across sectors like banking and healthcare that demand rock-solid authentication.
Voice authentication helps secure patient data and supports accurate voice-to-text documentation, which is crucial for tracking medical conditions and processing reimbursements. With US national health spending projected to hit $6.2 trillion by 2028, getting this right is essential.
Here’s how it’s being used on the ground:
- Physician Identity Verification: When a doctor e-prescribes medication, voice authentication can instantly verify their identity, ensuring only authorized personnel are writing scripts.
- Secure Telehealth Appointments: It’s a simple way for both the patient and the provider to confirm they’re speaking to the right person before a virtual visit begins, keeping the consultation private.
- Patient Data Access: A patient can securely access their own medical records over the phone or through a portal just by using their voice. It’s a much friendlier experience that doesn't sacrifice security.
Of course, with healthcare's strict rules, any new tech has to meet demanding standards. For anyone in this space, digging into the details of HIPAA compliant speech-to-text solutions is a crucial next step.
Enhancing Government and Retail Services
Beyond finance and healthcare, voice biometrics is also gaining traction in government and retail. Government agencies are using it to confirm citizens' identities for accessing things like social benefits or tax services, which cuts down on both fraud and administrative headaches.
In the retail world, it's all about personalizing the shopping experience and securing the rise of voice commerce. As more people use voice assistants to buy things, confirming the speaker's identity is the only way to prevent accidental or fraudulent purchases and build trust in this new way of shopping.
The Future of Identity Verification Is Your Voice
We've walked through how voice biometrics authentication pulls off a rare feat: delivering iron-clad security that feels completely effortless to the user. It’s a move away from things you know (like a password) to something you fundamentally are. Your unique voiceprint becomes the key, and this isn’t just an incremental update—it’s a whole new way to think about digital identity.
But this is far from the end of the story. The technology is always getting better, pushing the limits of how we can secure our digital lives. As we look to what's next, a few key developments are poised to weave voice authentication even deeper into our daily routines. The future isn't about just one biometric, but how they all play together.
The Rise of Multimodal Biometrics
The next frontier is what’s known as multimodal biometrics. Think of it as layering different security checkpoints on top of each other to create a security chain that’s nearly impossible to break. Imagine a system that recognizes not just your voice, but also your face and maybe even the specific way you hold your phone. This approach sends the already low odds of fraud plummeting, since a bad actor would have to mimic multiple biological and behavioral traits at the same time.
This layered security model gives us both flexibility and a much higher degree of confidence. For instance:
- Logging into an app? Your voice might be all that's needed.
- Transferring a large sum of money? The system might ask for both your voice and a quick facial scan.
This creates a smarter security framework that adjusts to the risk of the situation, applying just the right amount of protection without getting in your way.
Securing the Internet of Things
Our world is getting more connected by the day, and so are the security risks. The Internet of Things (IoT) is filling our homes, cars, and offices with smart devices. Trying to secure all of these gadgets with old-school passwords isn't just a hassle; it’s a non-starter. This is exactly where voice biometrics authentication is set to have a huge impact.
Your voice is becoming the universal remote for your life, and biometrics will ensure you're the only one in control. It's the password you can't lose, copy, or forget.
It won't be long before you’re using your voice to securely start your car, unlock your front door, or pull up sensitive files through a smart speaker. The technology offers a seamless and intuitive way to manage the growing web of devices we rely on.
Ultimately, your voice is becoming much more than a way to communicate. It's becoming a pillar of your digital identity, pointing toward a future where secure access is as simple and natural as just saying a few words.
Frequently Asked Questions About Voice Biometrics
When you're talking about a technology as personal as voice, it’s only natural to have a few questions. Understanding how voice biometrics authentication works behind the scenes is the best way to see its real-world value and how it keeps you secure. Let's tackle some of the most common ones.
How Secure Is Voice Biometrics Against Recordings and AI Deepfakes?
This is probably the number one question people ask, and for good reason. The good news is that modern systems are specifically designed to outsmart these kinds of attacks. They use a clever technique called ‘liveness detection’ to tell the difference between a live person and a playback.
Think of it this way: live speech has all sorts of tiny, subtle variations in frequency and acoustic patterns that a simple recording just can't replicate. The system is trained to catch those nuances.
On top of that, advanced AI can detect the tell-tale digital fingerprints left behind by deepfake or synthesized voices. These are microscopic inconsistencies and artifacts that are completely undetectable to the human ear but stand out clearly to the algorithm. This makes it exceptionally difficult for a fraudster to pass off a generated voice as the real thing.
Can a Cold or Loud Background Noise Cause It to Fail?
It’s a fair question—we’ve all had to deal with a scratchy throat or a noisy coffee shop. Fortunately, these systems are built to be remarkably resilient.
The technology focuses on the core physiological traits of your vocal tract—its unique size, shape, and structure. These are things that don’t change when you have a cold. The system is smart enough to filter out temporary hoarseness and lock onto those stable, underlying characteristics.
As for background noise, powerful AI noise-cancellation gets to work isolating your voice from whatever is happening around you. This ensures the system gets a clean signal to analyze, maintaining high accuracy even in a bustling office or call center. Of course, a good setup always helps. For some practical tips, check out our guide on how to set up your microphone for the best results.
What About Privacy? Is My Voice Being Recorded and Stored?
Privacy is non-negotiable, and any reputable system puts it first. A common misconception is that the system is storing audio files of your conversations, but that's not how it works. Your actual voice is never stored.
Instead, the system analyzes your speech and converts it into an encrypted, mathematical model. This digital representation is called a voiceprint.
A voiceprint is a secure digital template, not a recording. It's a series of numbers and data points that cannot be reverse-engineered to reconstruct your actual speech, ensuring your conversations remain private.
This one-way process is fundamental to responsible voice biometrics authentication. Top-tier providers also comply with strict data privacy laws like GDPR and CCPA, which set clear rules for how biometric data is handled. As the technology evolves, deep learning models are getting even better at distinguishing vocal traits while ignoring noise, opening up new, secure applications in banking, healthcare, and beyond.
Ready to bring voice-first efficiency and security to your legal work? Whisperit unifies dictation, drafting, and collaboration into a seamless AI workspace. Discover how you can move from intake to export faster at https://whisperit.ai.