Vendor Security Questionnaire Template Guide
A vendor security questionnaire is essentially a standardized checklist your organization uses to peek under the hood of a potential partner's security setup. It’s a core due diligence tool that helps you spot red flags and potential risks before they become your problem. Think of it as the foundation of any solid vendor risk management program.
Why a Solid Vendor Questionnaire Is Non-Negotiable
Let's get one thing straight: this isn't just about ticking a compliance box. In an era where supply chain attacks are everywhere, a vendor questionnaire is your first line of defense. When you bring a new vendor into your ecosystem, you're effectively handing them a key to your digital kingdom. Going in without vetting them properly is like leaving the door wide open.

This process isn’t about creating friction; it's about building trust and setting clear expectations from the get-go. A well-designed questionnaire shows your partners that you're serious about security and expect them to be, too. It gets everyone on the same page and helps sidestep messy security problems down the road.
Transforming Reactive Chaos into a Proactive Strategy
Trying to vet vendors with a random series of emails or a few off-the-cuff questions is a recipe for failure. It's inconsistent, a nightmare to track, and simply doesn't scale as your organization grows. A standardized vendor security questionnaire template brings order to that chaos, shifting your approach from reactive panic to proactive, strategic risk management.
When you use a consistent template, every vendor is measured against the same critical security benchmarks. This gives you an objective baseline for comparison, letting you make decisions based on data, not just a gut feeling. You're no longer guessing which vendor is more secure—you have the documentation to prove it.
A standardized questionnaire creates a clear, defensible record of due diligence. If a breach ever does occur, this documentation is your proof that you took reasonable and necessary steps to vet your partners—a crucial detail for any regulatory or legal scrutiny.
Before diving into the specific questions, it's helpful to understand the key areas you'll need to cover. A comprehensive questionnaire is built around several core security domains.
Here's a quick look at the essential components you'll want to include:
Core Components of an Effective Vendor Questionnaire
| Component Area | Objective |
|---|---|
| Information Security | To verify the vendor has established policies and controls to protect data confidentiality and integrity. |
| Data Privacy & Governance | To ensure compliance with regulations like GDPR or CCPA and confirm proper data handling procedures. |
| Access Control | To check how the vendor manages user access, permissions, and authentication to sensitive systems. |
| Incident Response | To understand the vendor's plan for detecting, responding to, and recovering from a security incident. |
| Physical Security | To assess the security of the vendor's physical facilities, like data centers and offices. |
| Business Continuity | To confirm the vendor has a solid plan to maintain operations during a disruption or disaster. |
These domains form the backbone of a strong assessment, ensuring you get a complete picture of a vendor's security posture.
The Real-World Consequences of Weak Vetting
The headlines are full of horror stories about massive breaches that started with a single compromised third-party vendor. A weak link in your supply chain can expose your entire organization, causing devastating financial losses and wrecking your reputation. Asking the right questions upfront can illuminate these critical vulnerabilities before you're locked into a contract.
The data paints a stark picture. Industry research shows that a staggering 74% of data breaches originate with third-party vendors. Yet, only about 42% of organizations bother with comprehensive security questionnaires during onboarding.
For those that do, the impact is huge. Companies using standardized questionnaires report a 68% reduction in vendor-related security incidents compared to those that don't. That's a massive difference.
Building a Foundation for Ongoing Risk Management
The initial questionnaire is more than a one-time onboarding task; it lays the groundwork for the entire vendor relationship. The vendor's answers give you a baseline snapshot of their security posture at that moment in time.
This initial data allows you to:
- Establish a Risk Baseline: Get a clear understanding of the vendor's security maturity from day one.
- Identify Areas for Improvement: Pinpoint specific controls that might be weak or need to be strengthened.
- Set the Stage for Continuous Monitoring: Use the initial answers as a benchmark for future check-ins and assessments.
Ultimately, a robust vendor security questionnaire isn't just a document—it's a strategic asset. It empowers you to protect your business, forge more secure partnerships, and make smarter, safer decisions. It helps you shift from putting out fires to preventing them from ever starting.
Building Your Vendor Security Questionnaire
Crafting a solid vendor security questionnaire template from the ground up can feel like a monumental task, but it’s much more approachable when you break it down into core components. The real goal here isn’t just to create a laundry list of questions; it's to build a logical framework that methodically uncovers specific risks. A truly effective questionnaire pushes past simple yes/no answers and makes vendors show you, not just tell you, about their security posture.
Thinking about it in a modular way helps. Each section is a building block representing a critical security domain. You can then assemble these blocks to create a full picture of a vendor’s defenses, adding or removing sections based on the specific risks that vendor introduces.
Information Security and Governance
This is your starting point—the foundation of the entire questionnaire. Here, you're trying to understand the vendor's big-picture security strategy, their official policies, and how they actually govern their security program. The questions in this section are all about figuring out if security is baked into their culture or just an inconvenient afterthought.
You need to know who’s in charge. Is there a CISO or someone in a similar role calling the shots? How often does security get a voice in front of executive leadership? The answers to these questions tell you a lot about how seriously the organization takes security and what kind of resources they put behind it.
- Policy Documentation: Don't just ask if they have a policy; ask to see it. Find out when it was last reviewed and updated.
- Employee Training: Dig into their security awareness training. How often are employees trained on things like phishing, proper data handling, and password hygiene?
- Compliance and Certifications: Does the vendor have any relevant certifications, like SOC 2, ISO 27001, or FedRAMP? If so, ask them to provide the reports or certificates.
Data Handling and Privacy
This section gets right to the heart of the matter: how a vendor collects, uses, stores, and eventually gets rid of your data. This is absolutely critical, especially if you’re sharing any kind of personally identifiable information (PII) or other sensitive data with them. Your questions need to be sharp and specific.
For instance, instead of asking a vague question like, "Do you protect our data?" get technical. Ask, "Describe the encryption standards (e.g., AES-256) used for our data both in transit and at rest." That forces a concrete answer. It's also vital to ask about your vendors' adherence to NIST SP 800-88 data sanitization standards to confirm they have a provable process for wiping data clean when it's no longer needed.
This is where regulatory compliance really comes into play. If your vendor will handle data from EU citizens, your questions must reflect GDPR requirements. The same goes for CCPA in California or HIPAA for protected health information.
In industries like healthcare, this level of scrutiny isn't just a good idea—it's essential. With 74% of healthcare data breaches tied to third-party vendors and over 275 million U.S. healthcare records compromised in a single year, the stakes are incredibly high. Current HIPAA rules now require things like multi-factor authentication, encryption, and annual audits, which makes every question you ask here even more important.
Access Control Measures
Poor access control is one of the most common ways breaches happen. This part of the questionnaire is all about evaluating how the vendor makes sure only the right people can access sensitive systems and data. What you're really looking for is proof they follow the principle of least privilege—giving people just enough access to do their jobs, and nothing more.
Here are a few key areas to probe:
- Authentication: Do they require multi-factor authentication (MFA) for everyone, especially for privileged accounts?
- Password Policies: What are their password rules? Think minimum length, character types, and how often they have to be changed.
- Access Reviews: How often do they actually audit who has access to what? This is how you catch former employees who still have active accounts or current employees with way too many permissions.
- Privileged Access Management (PAM): How do they manage and monitor the "keys to the kingdom"—those powerful administrative or root accounts?
These questions help you figure out if the vendor is actively minding the store or just leaving the doors wide open.
Incident Response and Business Continuity
Let's face it, no system is perfect. What really separates a prepared vendor from a risky one is how they plan for, detect, and respond when something goes wrong. This section dives into their readiness for a crisis and their ability to keep things running.
Your questions should focus on their documented plans. Ask for a rundown of their Incident Response Plan (IRP) and their Business Continuity/Disaster Recovery (BC/DR) plans. You absolutely need to know their process for notifying you if a breach affects your data, including their specific timelines for doing so.
A vendor's response here is a huge indicator of their maturity level. A mature partner will have well-documented, tested plans ready to go. A less mature one will give you vague answers, which is a massive red flag. The questions you ask here should map directly to the kind of controls outlined in a formal security control framework, which is the systematic way to manage these risks. For a deeper dive, you can check out our guide on how to implement a https://www.whisperit.ai/blog/security-control-framework.
Physical and Environmental Security
While we spend most of our time worrying about cyber threats, the physical security of a vendor’s buildings—especially their data centers—is just as critical. This section looks at the measures they have in place to protect physical hardware from theft, damage, or unauthorized access.
Consider asking about:
- Data Center Security: What kind of physical controls do they have at their data centers? Look for things like biometric scanners, 24/7 on-site security staff, and video surveillance.
- Environmental Controls: What systems do they have for fire suppression, climate control, and backup power (like UPS systems and generators)?
- Secure Office Policies: Do they enforce a "clean desk" policy to keep sensitive documents from being left out? How do they manage and track visitors?
By building your questionnaire with these distinct modules, you create a powerful and flexible tool. This structure ensures you get all the critical details you need to make a smart, risk-informed decision before you ever sign a contract.
Customizing Your Template for Real-World Risks
A generic, one-size-fits-all approach to vendor security just doesn't cut it. The risk from your cloud hosting provider is a completely different beast than the risk from your office coffee supplier. This is why tailoring your vendor security questionnaire template is a crucial strategic move, not just some procedural checkbox.
Blasting every single vendor with a monstrous 300-question document is the fastest way to get rushed, inaccurate answers and burn through goodwill. Smart risk management is about segmenting vendors into risk tiers and tailoring your questions to match. This targeted approach shows you respect your partners' time and lets your team focus its energy where it really counts: on the high-risk relationships.
This decision tree gives you a solid framework for tackling the core security areas as you start the vendor assessment process.
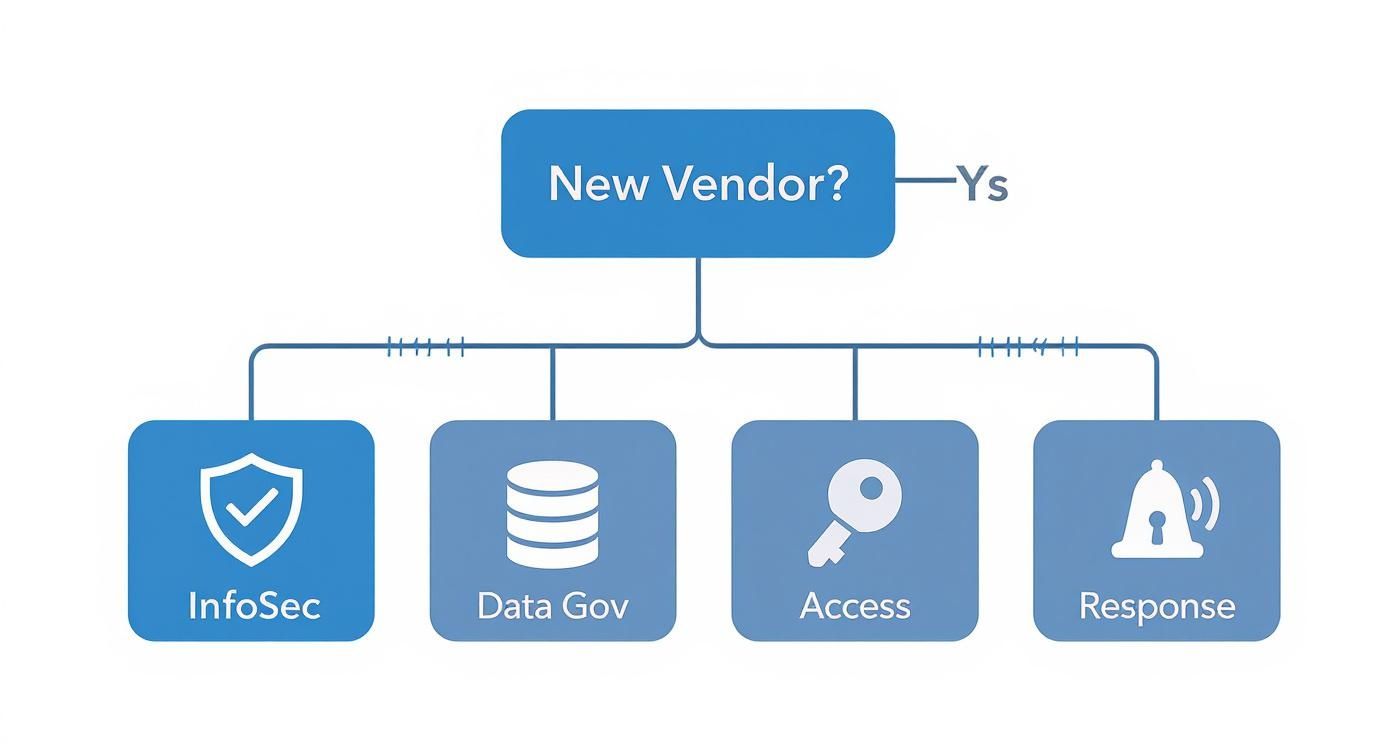
By branching out from that first contact into specific security domains, you can systematically customize your questions to hit the most relevant risk areas for each vendor.
Creating Risk Tiers for Your Vendors
First things first, you need to categorize your vendors based on the risk they introduce to your organization. This doesn't have to be a massive undertaking; a simple three-tier system is a fantastic place to start.
- Low-Risk Vendors: These are partners with little to no access to sensitive data or critical systems. Think of your office supply company, the landscaping crew, or a catering service. Their direct impact on your security is minimal.
- Medium-Risk Vendors: These vendors might touch non-critical but still important company data. This bucket often includes marketing automation platforms, project management tools, or specialized software that doesn't handle personal information.
- High-Risk Vendors: This is your most critical group. These are partners with deep access to sensitive data—like customer PII, financial records, or intellectual property—or your core network infrastructure. Cloud service providers, payment processors, and key software partners all fall in here.
Once these tiers are defined, you can build different versions of your questionnaire. The low-risk tier might get a super-lightweight set of 15-20 questions on basic security hygiene. The high-risk tier, on the other hand, gets the full, comprehensive deep-dive.
Aligning Questions with Vendor Services
Beyond just risk tiers, your questions have to align with the actual service being provided. It's pointless to ask your marketing agency about the physical fire suppression systems in their data center if they never store your data on-premise. Context is everything.
For instance, if you're bringing on a new SaaS provider, you’ll want to zero in on:
- Application security and their secure coding practices.
- Their cloud infrastructure security and access controls.
- How they handle data segregation in a multi-tenant environment.
Contrast that with a managed IT service provider. For them, you’d focus more on remote access protocols, endpoint security for their technicians' devices, and their privileged access management policies.
This kind of customization makes the whole process more efficient and gives you much more relevant information. It's quickly becoming the industry standard, with recent studies showing that around 75% of companies now use customized questionnaires. It's a clear shift away from generic templates toward a more intelligent, risk-based approach.
Deep Dives for High-Risk Relationships
For your high-risk vendors, a standard questionnaire is just the starting line. The real goal is to gather concrete evidence, not just take their word for it. This is where you have to ask for supporting documentation to validate their claims.
Don't just take their word for it. A "yes" on a questionnaire is an assertion; a third-party audit report is evidence. For high-stakes vendors, always ask for proof.
Here are the crucial documents you should be requesting:
- SOC 2 Type 2 Reports: This is the gold standard for verifying a vendor's security controls over time. Our guide on https://www.whisperit.ai/blog/soc-2-type-2-requirements breaks down exactly what to look for in these reports.
- Penetration Test Summaries: Ask for the executive summary from their most recent third-party pen test. This shows you how their defenses actually hold up against a simulated attack.
- Certifications: Things like ISO 27001 or other relevant industry certifications provide strong validation that they have a mature security program in place.
As you build out these custom templates, it's also smart to brush up on common threats. Understanding effective strategies to prevent Man-in-the-Middle attacks, for example, will help you ask sharper questions about how vendors protect data in transit. This ensures your questionnaire assesses not just their policies on paper, but their practical defenses against the real threats out there.
Analyzing Questionnaire Responses Like a Pro
So, you’ve gotten the completed questionnaire back from your vendor. That’s a great first step, but now the real work begins. What you're holding isn't just a form with a bunch of checked boxes; it's a blueprint of their entire security posture. Your job is to decode that blueprint and turn it into real, actionable intelligence for your risk management strategy.

Let's be clear: you're not looking for a "perfect" vendor. They don't exist. The goal here is to get a crystal-clear understanding of the specific risks this partnership introduces and decide if your organization can live with them. This calls for a methodical approach, mixing objective scoring with a bit of professional gut instinct.
Developing a Simple Scoring System
It’s easy to get lost in the weeds, trying to give every single answer the same weight. That's a fast track to analysis paralysis. Your best friend here is a simple, effective scoring system that lets you quickly triage responses and zero in on what truly matters.
I’ve always found that a basic three-point scale works wonders:
- 2 Points (Green): Solid answer. The vendor meets or even beats our requirements, and they’ve provided clear evidence to back it up.
- 1 Point (Yellow): This is a "maybe." The answer is a bit vague, or a control they have in place is weaker than we'd prefer. It needs a closer look.
- 0 Points (Red): Unacceptable response or a major red flag. This could be a straight-up "no" to a critical security control or an outright refusal to share necessary documents.
This system gives you an immediate visual and quantitative feel for the risk level. A questionnaire that's mostly green means you're likely on the right track. A sea of red and yellow, however, is a clear signal to hit the brakes and proceed with extreme caution—if at all.
Identifying Critical Red Flags
Not all answers are created equal. A weak password policy might be a yellow flag you can work on, but a vendor with no incident response plan? That's a deal-breaker. Part of the craft is learning to spot these critical issues right away.
Here are a few of the classic warning signs I always watch for:
- Vague or Evasive Answers: If you ask about encryption standards and they reply with, "We take security very seriously," that’s a massive red flag. It tells you they either don't know the answer or are hoping you won't notice they’re dodging the question.
- Refusal to Provide Documentation: Any legitimate, security-focused partner should be ready to share their SOC 2 report, recent pen test results, or key policies. If they're unwilling, you have to ask yourself what they're hiding.
- Inconsistent Responses: Do their answers contradict each other? For instance, they claim ISO 27001 certification but then describe a change management process that clearly violates the standard. Time to start digging.
- Lack of a Formal Incident Response Plan: This one is non-negotiable. A vendor without a documented, tested plan for what to do when things go wrong is a ticking time bomb for your business.
A vendor's response to your questionnaire is often a direct reflection of their security culture. Evasive answers and a lack of transparency during the assessment process are strong indicators of how they’ll behave if a real security incident occurs.
Digging into these responses is a crucial part of your overall security risk assessment. This questionnaire analysis slots right into that broader framework of identifying and mitigating threats to your organization.
The Power of Follow-Up Questions
The first round of answers is rarely the end of the story. Think of the initial questionnaire as a tool to uncover which topics need a deeper conversation. Your analysis should naturally produce a list of targeted follow-up questions to clear up any gray areas.
This isn't the time for a generic "Can you tell me more?" Be specific and show them you’ve done your homework.
| Initial Vague Response | Specific Follow-Up Question |
|---|---|
| "We conduct regular employee security training." | "What is the cadence of your security awareness training, what topics are covered, and how do you measure its effectiveness (e.g., phishing tests)?" |
| "Our data is encrypted." | "What encryption standards (e.g., AES-256) are used for our data at rest and in transit? How is key management handled?" |
| "We have a business continuity plan." | "Can you provide the RTO and RPO for the services you provide us? When was your BCDR plan last tested, and what were the results?" |
Asking questions at this level of detail accomplishes two things. First, it forces the vendor to provide concrete answers instead of marketing fluff. Second, it signals that you are a diligent and serious partner. This dialogue is your chance to see how their team responds under pressure and how willing they are to collaborate on security—qualities that are just as important as any single control they have in place.
Get Started With Our Free Vendor Security Questionnaire Template
Theory is great, but putting it into practice is what really matters. To give you a running start, we’ve put together a comprehensive, downloadable vendor security questionnaire template that’s built on all the best practices we’ve been talking about.
This isn’t just some generic list of questions I pulled off the internet. It's a strategic tool that I’ve refined over time, designed to be picked up, adapted, and put to use right away.
What’s Inside the Template
Think of this template as a framework for having better, more productive conversations with your vendors. I've structured it to be thorough enough for your high-risk partners but flexible enough to scale down for the little guys.
Here’s a quick look at the core sections:
- General Information: This part is for the basics—who are they, who do we contact, and what exactly are they doing for us?
- Security Governance: Here, we ask about their formal security program, what their policies look like, and how they train their own people.
- Data Handling & Privacy: This is where we get into the weeds on data classification, their encryption standards, and how they handle regulations like GDPR or CCPA.
- Access Control: This section focuses on the nitty-gritty of authentication methods, how they review user access, and the controls around privileged accounts.
- Incident Response & Business Continuity: We need to know they have a documented plan for when things go wrong and how they'll keep their services running.
How to Tailor It for Your Own Use
The real value here is in its adaptability. I designed it so you can easily chop it up for different risk tiers. For instance, with a low-risk vendor, you might just use the General Information section and cherry-pick a few key questions from Security Governance.
This template is your starting point, not the final word. The best security assessments are dynamic. Tailor the questions to align directly with the specific data and systems a vendor will access.
For your high-risk partners—the ones handling sensitive customer data—you'll want to use the entire document. More than that, you should be asking them for evidence, like their latest SOC 2 report or a summary of their most recent penetration test.
This whole approach fits perfectly into building a structured yet flexible risk assessment process. If you want to dive deeper into that side of things, check out our detailed guide on creating a vendor risk assessment template, which is the perfect companion to this questionnaire.
By starting with a solid vendor security questionnaire template like this one, you'll save a ton of time and make sure you’re asking the right questions from the get-go. This helps you move faster, make smarter decisions, and ultimately build a more secure supply chain.
Common Questions About Vendor Security Questionnaires
Even with the best template in hand, you're going to run into some real-world snags. It’s just the nature of the beast. Security and compliance teams often hit the same practical hurdles, from dealing with frustrated vendors to figuring out when to check back in with a partner you’ve worked with for years.
Let's walk through some of the most common questions that pop up and how to handle them.
How Long Should a Questionnaire Be?
This is the classic "it depends" answer, but for a good reason. The length of your questionnaire should be directly tied to the vendor's risk level. One of the biggest mistakes I see is teams blasting out a massive, 200-question document to every single vendor. That’s a surefire way to get rushed, sloppy answers and burn through goodwill.
A much smarter approach is to tier your questionnaires.
- Low-Risk Vendors: Keep it short and sweet. Think 15-25 questions. You're just confirming basic security hygiene and that they won't be touching sensitive data.
- Medium-Risk Vendors: This is your middle ground, probably around 50-75 questions. Here, you’ll dig into core security domains like access control and incident response, but you don't need to go into the weeds on every single control.
- High-Risk Vendors: For these partners, it's time for the deep dive. This questionnaire could easily be 100 to 300+ questions. When a vendor has the keys to the kingdom, you can't afford to cut corners.
The whole point is to be efficient. By matching the questionnaire’s depth to the actual risk, you show vendors you respect their time, which encourages them to give you better, more thoughtful answers.
How Should I Handle Pushback From Vendors?
Sooner or later, a vendor is going to say no. It’s especially common with large, mature companies that have their own security packet ready to go. They’ll often reply with something like, "We don't fill out custom questionnaires, but here’s our SOC 2 report and a link to our trust center."
Don't treat this as a roadblock. It's an opening for a conversation.
When a vendor sends their own security package, accept it as their first offer. Your next step is a gap analysis. Go through their documents and see what critical questions from your list they haven't answered. Then, you can go back with a much shorter, highly specific list of follow-up questions.
This tactic works because it shows you’ve actually reviewed their materials instead of just blindly sticking to a process. It turns a potential standoff into a collaborative effort to get the assurances you need. And for smaller vendors who might genuinely lack the resources for a long questionnaire, offering to hop on a call to review the most critical items can make all the difference.
How Often Should I Reassess Vendors?
Vendor security is never a one-and-done deal. A vendor’s security posture can—and will—change over time. They might change cloud providers, their team might turn over, or new vulnerabilities could emerge that affect their stack. An assessment at the start of the relationship is just the beginning.
You need to establish a reassessment schedule based on risk.
- High-Risk Vendors: Plan on a full reassessment annually. This means a fresh questionnaire and a request for their latest certifications and reports, like a new SOC 2 or pen test results.
- Medium-Risk Vendors: Checking in every 18-24 months is a solid cadence.
- Low-Risk Vendors: A light review every 2-3 years usually does the trick, unless there’s a major change in the services they provide you.
Putting this cycle in place ensures your understanding of third-party risk stays current. It helps you spot problems while they’re still small, long before they have a chance to become a full-blown security incident.
Streamline your entire legal workflow with Whisperit, the voice-first AI workspace that unifies dictation, drafting, and research. Move from intake to final export with greater speed and consistency. Discover how our secure, GDPR-aligned platform can transform your practice at https://whisperit.ai.