Security Risk Assessment Mastery: Your Complete Guide
Building Your Security Risk Assessment Foundation
Let’s face it, a lot of security risk assessments end up gathering dust. They become a check-the-box exercise instead of a valuable tool. Having chatted with countless CISOs and risk managers over the years, I've learned what truly makes a security risk assessment program effective. It all begins with a solid foundation.
This isn't about rigidly following a set of steps. It's about creating a security-focused culture within your organization. Start by setting clear objectives that directly support your business goals. Instead of using confusing technical jargon, explain the "why" of security in a way everyone understands. Focus on how security protects their work, their team, and the company’s success. For example, in healthcare, highlighting patient data privacy is much more impactful than discussing abstract threats.
When you’re building your security risk assessment foundation, understanding compliance requirements is essential. A great resource for this is the article on cloud security compliance. Your framework also needs to be flexible enough to adapt to your organization's changing needs. Think of it as a living document, not something you create once and forget. Regular reviews and updates are key, especially as your business grows and adopts new technologies.
One key thing to consider when assessing risk is the annual evaluation of global threats published by major organizations. For instance, the World Economic Forum's Global Risks Report 2025 highlights risks like environmental issues, economic instability, and technological disruptions. These reports are incredibly helpful for decision-makers, offering insights not only into current threats, but also potential future risks. The 2025 report particularly emphasizes how interconnected these risks are, meaning addressing one can have a knock-on effect on others. This broad perspective is essential when developing strategies to manage global security risks.
Common Pitfalls and How to Avoid Them
Creating a strong foundation also means knowing the common mistakes that can trip you up. One of the biggest is not getting buy-in from key stakeholders early on. If departments see the assessment as a painful audit, they won't be as cooperative. Instead, present it as a team effort to protect everyone's interests.
Another common mistake? Relying too much on generic templates and checklists. They’re fine as a starting point, but they often miss the unique aspects of your environment. Remember, security is not one-size-fits-all. Your assessment should be tailored to your organization—its industry, size, and specific vulnerabilities. If you’re looking for a good overview on conducting risk assessments, check out this article on how to conduct a risk assessment.
Finally, don’t treat your risk assessment as a one-and-done activity. Security is an ongoing process, not a destination. You need to incorporate continuous monitoring, review, and improvement. This means revisiting your assumptions, refining your processes, and adapting to the ever-evolving threat landscape. By avoiding these pitfalls and focusing on a strong foundation, you'll build a security risk assessment program that truly protects your organization.
Discovering What You Actually Need To Protect
You know that feeling, the one that keeps security professionals up at night? It's the chilling realization that you can't protect what you don't even know you have. A truly solid security risk assessment absolutely depends on a deep understanding of your assets. And I mean everything. We're talking servers, laptops, sure, but also those shadow IT projects lurking in the corners and that dusty old database nobody remembers (but that still holds sensitive data!). I've seen firsthand how these overlooked assets become a hacker's playground.
Unearthing Your Hidden Assets
Think of it like spring cleaning for your digital attic. You might be amazed at what you find tucked away. Uncovering your digital assets is often like that – revealing forgotten systems and network segments that are major security risks. I once worked with a company that discovered an entire server farm running an outdated operating system. Completely unpatched. Exposed to the internet. It was a ticking time bomb they were completely unaware of. Discovering vulnerabilities like this is the cornerstone of a good security risk assessment. And while you're at it, consider strong business security systems as part of your security foundation.
So, how do you find these digital dust bunnies? Automated tools are your friends here. They can scan your network and identify connected devices, giving you a good starting point. But don't rely on automation alone. Talking to different departments is key. They often have their own systems and software that IT isn't even aware of – those shadow IT projects I mentioned that can cause major security headaches.

Classifying Assets by Impact, Not Just Theory
Once you know what you have, you need to classify those assets based on their real business impact. This is where a lot of assessments go wrong. They focus on theoretical importance, not real-world consequences. Sure, a database with customer credit card info is critical. But what about that file server with employee performance reviews? A breach there could be just as damaging to your reputation and could even lead to legal trouble.
This is where a solid asset classification framework comes in. Think about factors like confidentiality, integrity, and availability. Even a simple framework (high, medium, low impact) can be powerful if you clearly define the criteria for each category. Let me show you what I mean. The following table outlines a sample framework:
To help illustrate this, let’s look at a practical example of how you might categorize your assets:
Asset Classification Framework
| Asset Type | Classification Level | Security Requirements | Assessment Frequency | Responsible Team |
|---|---|---|---|---|
| Customer Database | High | Encryption, Multi-Factor Authentication, Regular Backups | Monthly | Security Team |
| File Server | Medium | Access Control Lists, Regular Security Patching | Quarterly | IT Department |
| Marketing Website | Low | Web Application Firewall, Regular Vulnerability Scanning | Annually | Marketing Team |
This framework allows you to tailor your security measures based on the criticality of each asset.
Navigating the Politics of Asset Discovery
Let's be honest, asset discovery can be tricky. You might encounter resistance from departments who are hesitant to disclose everything they have. They might be worried about being judged or fear increased scrutiny. This is where good communication and collaboration are essential. Explain why you're doing the assessment and how it benefits everyone. Emphasize that the goal is improvement, not blame.
Building a culture of transparency is crucial. Encourage open communication and make it clear that sharing information is a good thing. Sharing success stories can help. For example, talk about a company that found a vulnerability in a forgotten system and prevented a major data breach because they were proactive.
Finally, remember your asset register isn't a "set it and forget it" document. It needs to evolve as your organization does. Regularly update your inventory and refine your classification framework to reflect your current environment. This ongoing effort will ensure your security risk assessment stays relevant and keeps your valuable assets protected.
Mapping Your Real Threat Landscape

Think of generic threat lists like a generic map: they show the basics, but miss the crucial details specific to your business. A truly effective security risk assessment needs to dive deeper, mapping the threats likely to happen, given your unique situation. A small online retailer and a multinational bank? Totally different threat landscapes. Their security investments should reflect that.
Threat Modeling: Focusing Your Defenses
Smart security teams don't try to defend against everything; it's just not feasible. Instead, they use threat modeling to prioritize. Threat modeling involves asking key questions: Who’s most likely to target us? What are their motivations? What vulnerabilities might they exploit? A good threat model isn't about hypothetical "what ifs." It's grounded in a real-world understanding of your organization’s strengths and weaknesses, and the attackers who might be interested. For example, if your company relies heavily on cloud services, you should focus on cloud-specific vulnerabilities like misconfigurations and access control issues.
Knowing industry-specific threat patterns is also critical. Are you in healthcare, finance, or retail? Each sector has its own unique set of adversaries and attack vectors. Knowing the common tactics in your industry gives valuable context for your risk assessment. Understanding what makes your organization an attractive target—intellectual property, customer data, financial resources—helps you focus your defenses where they matter most.
The U.S. Intelligence Community's Annual Threat Assessment (ATA) for 2025, for instance, provides invaluable insights into the evolving threat landscape, covering both non-state actors like criminals and terrorists, as well as state-sponsored activities. The report details the increasing sophistication of these threats and the importance of proactive security. Want to know more? Check out the full report.
Beyond the External: Internal Risks and Supply Chain Vulnerabilities
External threats grab headlines, but don't forget internal risks. Insider threats, whether intentional or accidental, can be just as damaging. Think: a disgruntled employee leaking sensitive data, or a careless mistake causing a breach. Your risk assessment needs to address these internal vulnerabilities head-on.
Your supply chain is another increasing risk area. Do your vendors have strong security practices? A vulnerability in their systems could easily become your problem. A thorough assessment should evaluate your supply chain’s security posture, including incident response and data protection.
Keeping Your Threat Intelligence Actionable
Building a threat model isn’t a one-and-done activity. The threat landscape is constantly evolving, so your intelligence needs to stay current and actionable. This means setting up processes for gathering threat information, analyzing its relevance, and updating your security strategy.
Clear communication is essential, too. Translate complex threat information into language that executives and board members can grasp. Focus on the potential business impact of different threats to enable informed decisions about resources and risk mitigation. A well-defined security risk assessment helps your organization make proactive, data-driven decisions that strengthen your security and protect your valuable assets.
Finding Vulnerabilities That Actually Matter

Let's be real, those scanner reports packed with thousands of potential problems? More confusing than helpful. They drown you in data, making it nearly impossible to pinpoint what truly needs fixing first. A good security risk assessment isn't about finding every single theoretical crack. It's about finding the ones that pose a real danger to your business.
Prioritizing What Truly Matters
Seasoned security pros know how to sift through the clutter. They don't just fixate on a vulnerability's CVSS score. They consider exploitability, business impact, and realistic threat scenarios.
For example, a critical vulnerability in a system open to the internet is way more urgent than the same vulnerability on an internal, isolated system. It's all about putting your resources where they'll do the most good, protecting your business from the biggest threats.
Cybersecurity is crucial, and reports like the CrowdStrike 2025 Global Threat Report offer valuable insights into the latest cyber threats. In 2022, the average cost of a data breach topped $4.35 million globally—a stark reminder of how expensive vulnerabilities can be.
Think about it: a hard-to-exploit vulnerability with a minor potential impact? Not your top priority. But a vulnerability that's easy to exploit and could seriously disrupt your business? That's where you need to focus.
Automated Tools vs. Manual Assessment
Automated vulnerability scanners are handy for initial checks, but they're not a replacement for human insight. They can flag a lot of potential problems, but they often miss the specific quirks of your environment. That's where manual assessment shines. Manual testing can unearth vulnerabilities that automated tools miss, especially tricky things like logic flaws in web apps or misconfigurations in cloud environments.
I remember working with a client whose automated scan looked perfect. But a manual check revealed a critical authentication bypass. Talk about a close call! Understanding electronic eavesdropping risks is also essential, something you can learn more about through TSCM bug sweeps.
Testing Your Defenses and the Human Element
A real-world security risk assessment goes beyond just technical vulnerabilities. Are your security controls actually doing their job? Penetration testing helps you confirm that your firewalls, intrusion detection systems, and other security measures are stopping attacks. Vendor risk management is another important aspect to consider.
And never forget the human element. People are often the weakest link. Social engineering can bypass even the toughest tech defenses. Assessing user awareness and security practices through phishing simulations or security training is vital.
Similarly, don't overlook procedural weaknesses. Are there holes in your incident response plan? Do your employees know what to do if they suspect a breach? Attackers love exploiting these weaknesses.
Responsible Disclosure and Vendor Coordination
Finally, a good assessment includes a plan for what to do after finding vulnerabilities. This means understanding responsible disclosure and knowing how to work with vendors when you find problems in their products. It's about building relationships and fixing problems quickly. This proactive approach fosters trust and makes everyone more secure.
Creating Risk Assessments That Drive Real Decisions
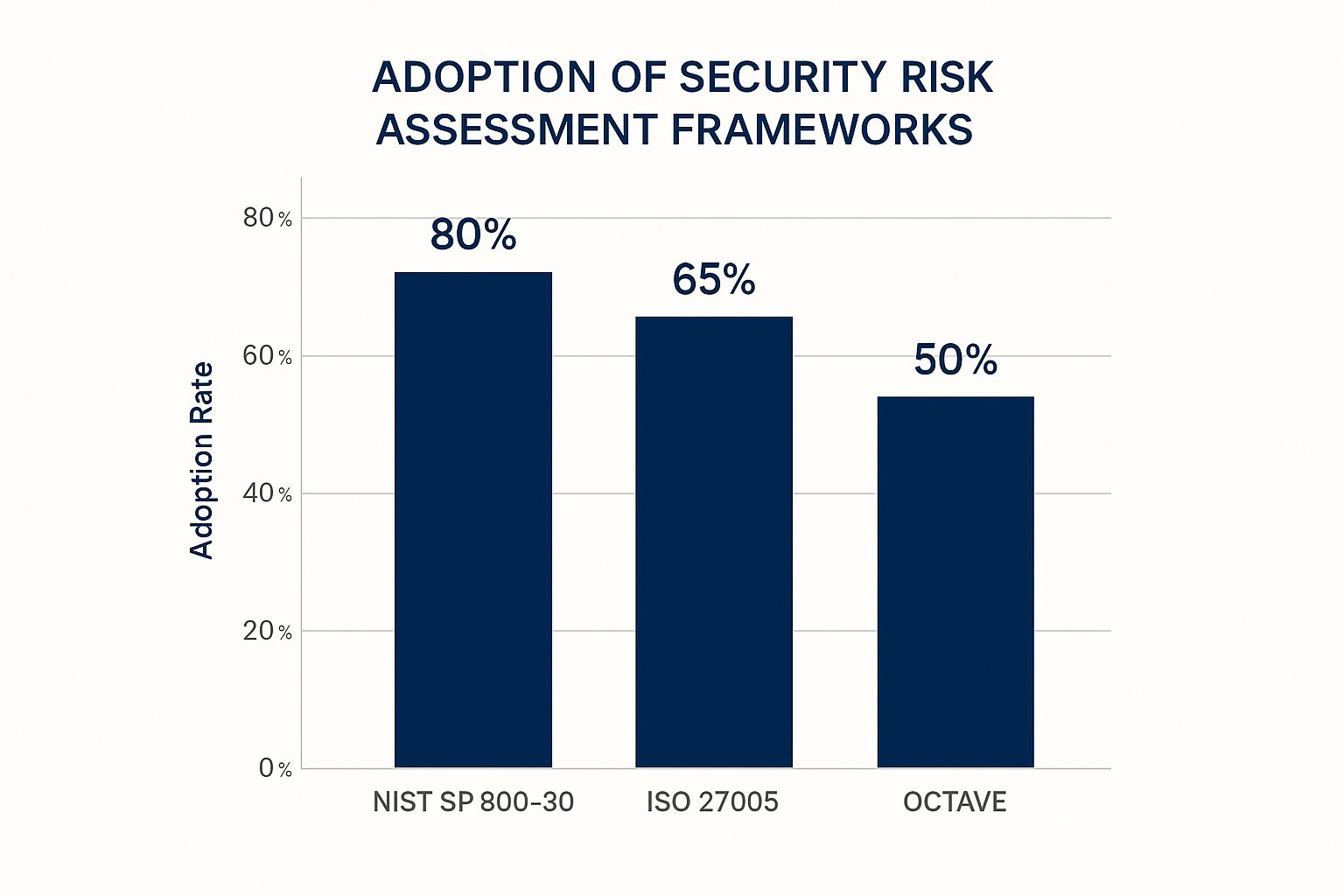
The infographic above shows how many folks are using different security risk assessment frameworks. 80% are rocking the NIST SP 800-30, 65% are using ISO 27005, and 50% are working with OCTAVE. NIST is clearly popular, but it's cool to see the mix. The key takeaway? There are plenty of solid options available.
Too often, risk assessments end up as pretty heat maps that gather dust on a shelf. They look impressive, but they don’t actually help anyone make smart decisions. That's not what we want. A security risk assessment should be a living, breathing document that informs security investments and resource allocation. Let's talk about how to make that happen.
Designing Risk Scoring for Your Organization
Lots of organizations just grab a generic industry standard for risk scoring. While there’s some value in those standards, a truly effective system needs to reflect your organization's specific risk appetite. What’s acceptable for one company might be a disaster for another. Think about your core business priorities. What keeps the CEO up at night? What scenarios would cause the most disruption?
For example, a small startup and a massive bank have totally different risk tolerances. Their scoring systems should reflect that. I've seen this play out firsthand. Misaligned risk scoring can lead to wasted money on minor issues while leaving gaping holes in your security posture. You want to fix what really matters.
Quantifying Risk: Moving Beyond Guesswork
Ditch the subjective gut feelings. You need a way to quantify risks so everyone, especially executives, understands and trusts the process. A common approach is to estimate the probability of a threat and its potential impact. Assign numerical values to each, maybe on a scale of 1-5 or 1-10. Make sure the definitions for each level are crystal clear.
What does a “high” impact actually mean? Maybe it's a financial loss of over $1 million, a PR nightmare, or a major regulatory penalty. Clearly defining these levels removes the guesswork and ensures consistent scoring. It also makes your recommendations much more defensible.
Presenting Risk Information Effectively
Even the most brilliant analysis is useless if no one understands it. A dry, jargon-filled report won't resonate with executives. You need to communicate clearly and concisely, translating tech-speak into business impact. Focus on how potential security breaches could affect revenue, reputation, and operations. Frame it in a way that resonates with their business objectives.
I once worked with a company that struggled to get executive buy-in for crucial security investments. Their reports were just too technical. We revamped their reporting, using visuals and plain language to highlight the business consequences of inaction. The change was dramatic. Executives finally grasped the risks and approved the funding. Simple things like a security audit checklist can also help streamline the process.
Here’s a simple template to help you get started:
Risk Scoring Matrix Template
A practical risk assessment matrix showing probability levels, impact categories, and corresponding risk scores with recommended actions
| Probability | Impact Level | Risk Score | Recommended Action | Timeline |
|---|---|---|---|---|
| Low | Low | Low | Accept | N/A |
| Low | Medium | Medium | Monitor | 6 Months |
| Low | High | High | Mitigate | 3 Months |
| Medium | Low | Medium | Monitor | 6 Months |
| Medium | Medium | High | Mitigate | 3 Months |
| Medium | High | Critical | Mitigate Immediately | 1 Month |
| High | Low | High | Mitigate | 3 Months |
| High | Medium | Critical | Mitigate Immediately | 1 Month |
| High | High | Critical | Mitigate Immediately | 1 Week |
This matrix makes it easy to visualize which risks demand immediate attention and where to allocate your resources. Remember, your security risk assessment should be a living document, constantly adapting to the changing threat landscape and your organization's evolution. By communicating effectively and using a well-defined framework, your assessments become powerful tools for continuous improvement and informed decision-making, ensuring your business is well-protected.
Turning Assessment Results Into Action
Let's be honest, a security risk assessment that gathers dust on a shelf isn't worth much. The real value comes from transforming those findings into a practical, actionable plan. This section is all about making sure that happens – that your assessment leads to real improvements, not just a checklist exercise. It boils down to smart prioritization, considering your risks, resources, and the unavoidable realities of your business.
Prioritizing Remediation Efforts
You've identified your vulnerabilities, now what? You can't fix everything at once, so prioritization is essential. Start with the highest-risk items: the vulnerabilities most likely to be exploited and cause the most damage. Imagine a burglar casing a house – they're going to go for the easiest entry point with the biggest potential payoff, right? Same principle here.
Resource limitations are a fact of life. Do you have the budget, the team, and the tools to address every single vulnerability? Probably not. Be realistic about what you can achieve and set achievable goals. Focus on the biggest wins first.
Business needs also play a crucial role. Sometimes, security improvements have to take a back seat to other priorities. You might need to defer certain fixes or implement temporary workarounds. I remember working with a company that desperately needed a firewall upgrade, but a major product launch was imminent. We put in temporary compensating controls until the launch was over, then tackled the firewall. It's a balancing act.
Exploring Risk Treatment Approaches
Think of dealing with risk like playing a hand of cards. You have a few options: mitigation, acceptance, avoidance, and transfer. Mitigation is like trying to improve your hand – reducing the risk to an acceptable level. Think patching vulnerabilities, implementing strong passwords, and encrypting sensitive data.
Acceptance is like deciding to play your hand as is – acknowledging the risk and living with it. This is usually done when the cost of mitigation outweighs the potential impact. Avoidance is like folding your hand altogether – eliminating the risk entirely. This might mean decommissioning a vulnerable system or avoiding a risky business venture.
Finally, transfer is like getting someone else to play your hand – shifting the risk to a third party. This could involve buying cyber insurance or outsourcing security functions. The right approach depends on your specific circumstances and risk tolerance.
For more detail on mitigating security risks, our guide on data security best practices can be a helpful resource.
Building Accountability and Tracking Progress
A good security risk assessment program is built on accountability. Who's responsible for implementing which fixes? What are the deadlines? How will you track progress? Regular reporting is essential. Keep stakeholders in the loop on what's been done, what's outstanding, and any challenges you've faced.
Maintaining momentum can be a challenge, especially when security competes with other business priorities. Celebrate your successes! This keeps everyone motivated and reinforces the idea that security is everyone's responsibility. Regular communication and transparent reporting are crucial for keeping everyone informed and engaged. Security is an ongoing journey, not a destination.
Keeping Your Assessment Program Alive And Relevant
A security risk assessment isn't a one-off; it's a living, breathing process. It needs to adapt as your organization grows and the threat landscape shifts. The key is building a program that consistently delivers value without turning into a monster you dread. Let's talk about how to make that happen.
Scheduling Regular Assessments
So, how often should you run a security risk assessment? Honestly, it depends. A fast-growing tech startup adding new tech every other week needs a more frequent cadence than an established business with a stable infrastructure. Tie your assessments to your organization's rhythm of change—new projects, system upgrades, new vendors—and they’ll stay relevant. This way, assessments become a natural part of how you operate, not a separate, painful chore.
You might be interested in: Cloud Security Compliance Standards
Monitoring and Adapting to Shifting Risks
Let's be real, the threat landscape is a constantly moving target. New vulnerabilities pop up daily, and attackers are always cooking up new tricks. Your security risk assessment program needs to keep pace. Regularly check threat intelligence feeds and industry reports. Subscribing to vulnerability databases and security newsletters can be incredibly helpful. Use this intel to update your assessment framework and prioritize your security efforts based on what’s actually happening out there.
The NIST Cybersecurity Framework is a great resource for managing and mitigating cybersecurity risk. The image below visualizes the framework's core components:
This framework champions a proactive approach. It encourages organizations to identify, protect, detect, respond, and recover from cybersecurity incidents. Aligning your program with the NIST framework can build a more resilient security posture.
Building Internal Capabilities and Documentation
Developing in-house expertise is crucial. Training your team on assessment methodologies, threat modeling, and vulnerability analysis gives them ownership of the process. I’ve personally seen how empowering internal teams makes for a more proactive and effective security approach. And don't underestimate good documentation. Clear guidelines, templates, and checklists keep assessments consistent, even as team members change.
Measuring Program Effectiveness and Continuous Improvement
How do you know your program is working? You need to measure it! Track things like the number of vulnerabilities identified and fixed, the time it takes to resolve issues, and the overall improvement in your security posture. When you report progress to stakeholders, speak their language. Focus on business impact, not just technical details. For example, showing how the program has reduced the risk of data breaches or avoided regulatory fines will resonate more with executives than a list of patched vulnerabilities. Regularly review your program, looking for ways to make it better. Learn from past assessments, incorporate industry best practices, and be ready to adapt. That’s how you build a program that continuously delivers value and keeps your organization secure.
Ready for a smoother, more secure way to handle documents? Whisperit, the AI-powered dictation and text editing platform, helps professionals in legal, healthcare, and other security-conscious sectors streamline workflows and boost productivity while keeping data privacy top of mind. Check it out!