8 Essential Penetration Testing Best Practices for 2025
In the complex digital landscapes of legal, healthcare, and compliance-driven sectors, a reactive security posture is no longer sufficient. Proactive defense requires rigorous, methodical, and ethical testing to uncover vulnerabilities before malicious actors can exploit them. The challenge extends far beyond simply running an automated scan; it's about adopting a strategic framework that ensures comprehensive coverage, minimizes operational risk, and delivers actionable intelligence to stakeholders. For organizations handling sensitive client data, protected health information (PHI), or financial records, adopting mature penetration testing best practices is not just a technical necessity, but a critical component of risk management and regulatory adherence.
This guide moves beyond generic advice to provide a detailed roadmap for building a resilient and defensible security program. We will dissect eight critical best practices that transform security testing from a compliance checkbox into a cornerstone of your cyber defense strategy. By focusing on meticulous planning, controlled execution, and clear communication, you can ensure your testing efforts yield maximum value and keep sensitive data protected against sophisticated threats.
Readers will learn how to implement a structured approach covering:
- Proper Scope Definition and Authorization
- Comprehensive Reconnaissance and Information Gathering
- Risk-Based Vulnerability Assessment and Prioritization
- Methodical Testing Methodology Following Industry Standards
- Safe and Controlled Exploitation Techniques
- Comprehensive Documentation and Evidence Management
- Professional Reporting and Executive Communication
- Continuous Retesting and Remediation Validation
1. Proper Scope Definition and Authorization
The most critical, foundational element of any ethical hacking engagement is establishing a meticulously defined scope and securing explicit, written authorization. This is not merely a formality; it is the legal and operational bedrock upon which the entire penetration test is built. An improperly defined scope can lead to severe consequences, including testing the wrong assets, causing unintended operational disruptions, and creating significant legal liabilities for both the testing team and the client.

This initial phase acts as the formal Rules of Engagement (RoE). It dictates precisely what systems, networks, IP ranges, applications, and physical locations are permissible targets. It also clarifies what methods are allowed (e.g., social engineering, denial-of-service testing) and which are strictly forbidden. A well-documented scope prevents scope creep and ensures the engagement aligns perfectly with the organization's business objectives and risk tolerance. Without this clarity, a penetration test is just unauthorized hacking.
Why It's a Top Best Practice
In regulated industries like healthcare and finance, the stakes are exceptionally high. A misstep can result in HIPAA or PCI-DSS violations, leading to massive fines and reputational damage. Proper authorization, often requiring sign-off from senior leadership or even the board, provides a legal "get out of jail free" card for the testers and protects the organization by demonstrating due diligence. This formal agreement is a cornerstone of professional penetration testing best practices.
Implementation Tips
To ensure your scope is robust and legally sound, follow these actionable steps:
- Obtain Written Approval: Never begin testing based on a verbal agreement. Secure a signed document from an individual with the proper authority to approve such an activity.
- Define Testing Windows: Specify exact dates and times when testing is permitted. For a healthcare provider, this might mean avoiding tests on critical patient systems during peak operational hours.
- Establish Communication Channels: The scope document must include emergency contact information for both the testing team and the client, along with clear escalation procedures for critical findings or unexpected system issues.
- Be Explicit with "Out-of-Scope": Clearly list all systems, third-party services, and networks that are explicitly forbidden to test. This prevents accidental targeting of production environments or partner systems.
Developing a comprehensive scope document is a detailed process. For a structured approach, you can find a helpful project scope template to guide your planning. Using a standardized format ensures no critical details are overlooked, providing a solid foundation for a successful and secure engagement.
2. Comprehensive Reconnaissance and Information Gathering
Often overlooked as a preliminary step, the reconnaissance phase is where the most skilled penetration testers lay the groundwork for a successful engagement. This is the intelligence-gathering stage, where testers systematically collect information about target systems, networks, and personnel using a combination of passive (non-intrusive) and active (interactive) techniques. This foundational work provides the critical intelligence needed to build effective testing strategies and identify potential, often hidden, attack vectors before launching any exploits.

Think of this phase as a detective's investigation. It involves mapping the target's digital footprint to understand its structure, technologies, and even its human element. This could range from discovering exposed IoT devices on a corporate network using Shodan, to researching an organization’s hierarchy on LinkedIn to prepare for a targeted social engineering attempt. The more comprehensive the information gathered here, the more precise and impactful the subsequent testing phases will be. A thorough reconnaissance effort is a hallmark of professional penetration testing best practices.
Why It's a Top Best Practice
In sensitive environments like healthcare or finance, a "brute force" approach to testing is reckless and can cause severe operational disruptions. Reconnaissance allows for a surgical approach, identifying high-value targets and likely weak points without generating excessive noise that could trigger alarms or impact critical systems. For example, discovering a misconfigured DNS zone transfer could expose an entire internal network architecture, allowing a tester to bypass perimeter defenses entirely. This initial investment of time drastically increases the efficiency and effectiveness of the penetration test.
Implementation Tips
To execute a thorough and stealthy reconnaissance phase, integrate these actionable steps into your methodology:
- Start Passively: Begin with passive techniques that do not directly interact with the target's infrastructure. Use open-source intelligence (OSINT) tools, search engine dorking, and public records to gather data without alerting defensive systems.
- Leverage Diverse Sources: Corroborate findings by using multiple information sources. Combine data from tools like Shodan, public WHOIS records, social media, and job postings to build a more complete picture of the target's assets and technologies.
- Document Everything: Meticulously record all findings, no matter how small they seem. An old email address or a forgotten subdomain discovered during this phase could become a key entry point during exploitation.
- Respect Technical Limits: When transitioning to active reconnaissance (like port scanning), be mindful of rate limits and firewall rules. Overly aggressive scanning can trigger security controls, block your IP address, or even cause a denial-of-service condition on sensitive equipment.
3. Risk-Based Vulnerability Assessment and Prioritization
A penetration test can uncover hundreds of vulnerabilities, but not all of them pose the same level of threat to the organization. A risk-based approach moves beyond simply cataloging findings and instead systematically analyzes and ranks them based on their potential business impact, the likelihood of exploitation, and the technical severity. This ensures that finite remediation resources are directed toward the most critical security gaps first, maximizing the return on security investment.
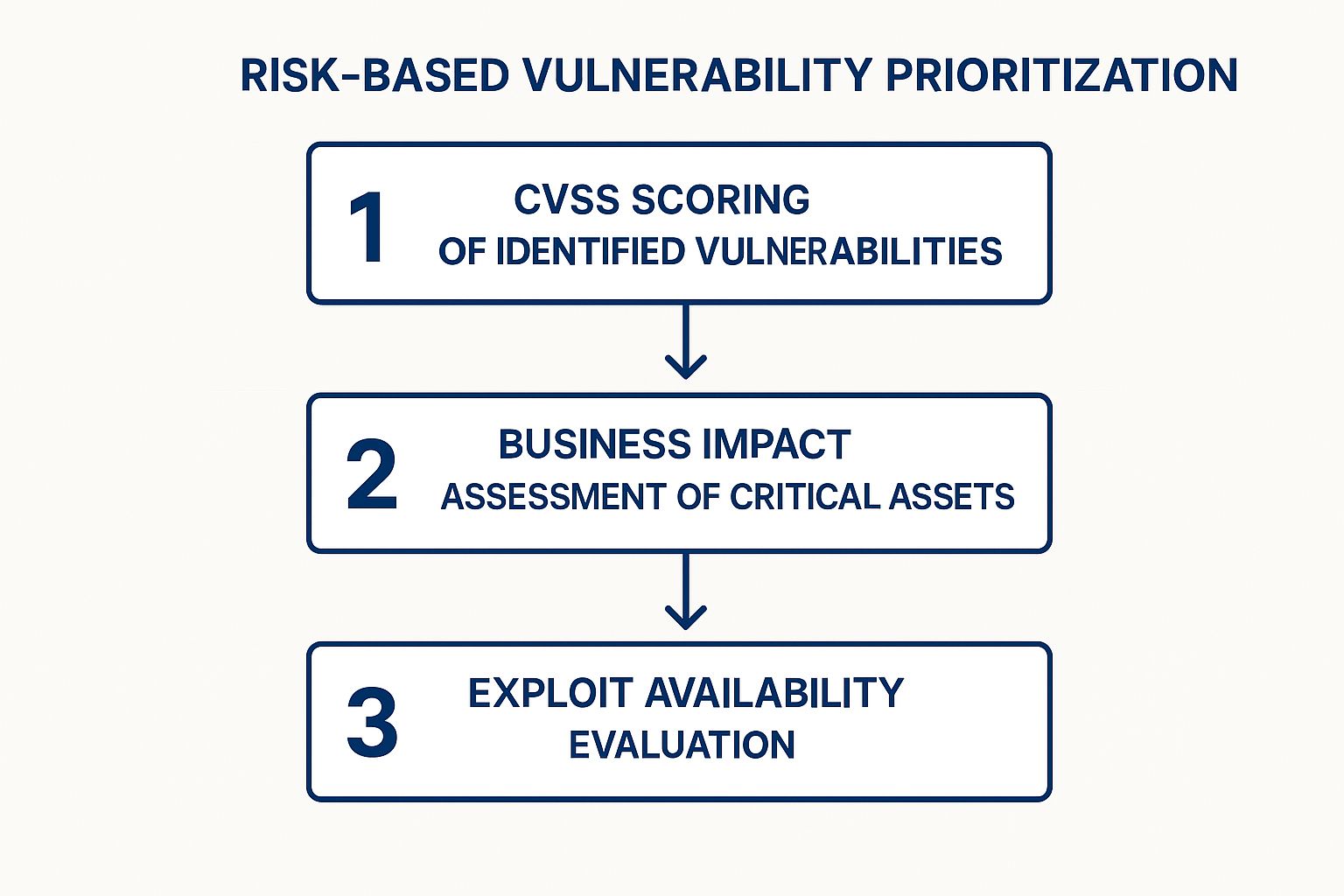
This method involves a disciplined process of evaluating each vulnerability within its specific business context. For instance, an SQL injection flaw in a public-facing e-commerce application that processes patient or financial data represents a far greater risk than a low-impact cross-site scripting (XSS) vulnerability on an internal, non-critical documentation server. By prioritizing this way, organizations can address the threats that truly matter. The infographic above visualizes this sequential process, starting with technical scoring and layering on business context. This flow demonstrates how combining technical severity with business impact and exploitability creates a true risk profile.
Why It's a Top Best Practice
In high-stakes environments like healthcare and finance, a minor technical flaw in a critical system can lead to catastrophic data breaches, regulatory fines, and operational collapse. A risk-based approach provides a defensible and logical framework for decision-making. It enables security teams to clearly communicate to leadership why certain issues require immediate attention, translating technical jargon into tangible business risk. This alignment is a hallmark of mature security programs and one of the most effective penetration testing best practices.
Implementation Tips
To effectively implement a risk-based assessment, integrate the following steps into your process:
- Combine Technical Severity with Business Context: Don't rely solely on automated scanner ratings. Use a standardized framework like the Common Vulnerability Scoring System (CVSS) as a baseline, then adjust the priority based on the business criticality of the affected asset.
- Involve Business Stakeholders: The IT and security teams understand the technical severity, but only business unit leaders can accurately assess the impact of a system compromise. Involve them in the risk evaluation process to get a complete picture.
- Utilize Diverse Testing Methods: A comprehensive understanding of your risk landscape is enhanced by using a mix of security testing methods. Incorporating DAST and SAST tools during the development lifecycle can help identify and categorize weaknesses early, feeding valuable data into your risk assessment.
- Factor in Exploitability: Consider the threat landscape. Is there a publicly available exploit for the vulnerability? Is it being actively targeted by threat actors? A vulnerability with a known, easy-to-use exploit should be prioritized higher.
Adopting this strategic approach requires a structured methodology. To build a robust framework, it is beneficial to learn more about a comprehensive security risk assessment process.
4. Methodical Testing Methodology Following Industry Standards
Ad-hoc, unstructured testing is a recipe for incomplete results and missed vulnerabilities. A core tenet of professional penetration testing best practices is adherence to an established, methodical framework. Leveraging industry-standard methodologies like the Penetration Testing Execution Standard (PTES), OWASP Testing Guide, or NIST Special Publication 800-115 provides a structured, repeatable, and comprehensive approach to security assessments. These frameworks ensure that testing isn't just a random series of attacks but a systematic process covering all critical phases, from intelligence gathering to post-exploitation and reporting.
These methodologies act as a roadmap for the engagement, ensuring consistency and quality across different tests and testers. For a financial institution, following a NIST-aligned methodology provides a defensible and auditable trail for regulators. Similarly, testing a web application against the OWASP Top 10 using the OWASP Testing Guide ensures that the most common and critical web vulnerabilities are systematically checked. This structured approach moves penetration testing from an art to a science, yielding more reliable and valuable results.
Why It's a Top Best Practice
Adopting a formal methodology elevates the credibility and defensibility of a penetration test. In a legal or compliance context, being able to demonstrate that testing followed a recognized industry standard is crucial for proving due diligence. It shows that the organization took a thorough and professional approach to security validation, rather than simply "poking around." This structured process guarantees comprehensive coverage, minimizing the risk of overlooking critical vulnerabilities that an unstructured test might miss.
Implementation Tips
To effectively integrate standard methodologies into your testing process, consider these actionable steps:
- Select the Right Framework: Choose a methodology that aligns with your specific objectives. Use the OWASP Testing Guide for web applications, NIST SP 800-115 for general network security assessments, and PTES for a comprehensive, end-to-end engagement.
- Customize for Your Context: While standards provide an excellent foundation, customize them to fit your organization's specific technology stack, industry regulations (like HIPAA or PCI-DSS), and risk profile.
- Document the Process: Clearly document which methodology is being used and any specific customizations made within the Rules of Engagement. This provides clarity and a solid basis for the final report.
- Combine Methodologies for Depth: Don't be afraid to blend frameworks. For instance, you could use PTES as the overarching structure for an engagement while integrating specific testing techniques from the OWASP guides for web components.
For a deep dive into one of the most respected frameworks, the PTES Technical Guidelines provide a detailed, seven-phase approach that can serve as an excellent starting point for building a robust internal testing program.
5. Safe and Controlled Exploitation Techniques
Once vulnerabilities are identified, the temptation can be to demonstrate their full impact through aggressive exploitation. However, a core tenet of professional penetration testing best practices is to prove the risk without causing actual harm. Safe and controlled exploitation involves using just enough force to validate a vulnerability's existence and potential impact while meticulously avoiding system damage, data corruption, or service disruptions that could affect business operations.

This practice is about demonstrating proof-of-concept rather than executing a full-scale attack. For example, instead of exfiltrating an entire customer database to prove a SQL injection flaw, a tester would retrieve a single non-sensitive record or the database version number. This approach provides irrefutable evidence for the remediation team without exposing sensitive data or destabilizing the production database. It is the critical difference between ethical hacking and malicious activity.
Why It's a Top Best Practice
In sensitive environments like healthcare or legal firms, the integrity and availability of data are paramount. An uncontrolled exploit could crash a critical patient record system or expose confidential client information, leading to catastrophic operational and legal consequences. By adopting a "do no harm" philosophy, penetration testers build trust and ensure the engagement adds value by identifying risks, not creating new ones. This responsible approach is non-negotiable for maintaining professional integrity and ensuring client safety.
Implementation Tips
To execute exploits safely and effectively, integrate these steps into your methodology:
- Establish Proof-of-Concept Goals: Before attempting an exploit, define the minimum evidence needed. This could be creating a harmless file (e.g.,
C:\pentest.txt), taking a screenshot of a restricted directory, or adding a temporary, non-privileged test account. - Prioritize System Backups: Always confirm with the client that recent, validated backups of target systems exist before any exploitation activities begin, especially on critical infrastructure.
- Coordinate with System Owners: For high-risk systems, schedule exploitation attempts during approved maintenance windows and maintain a direct communication line with system administrators who can monitor for adverse effects.
- Practice Immediate Cleanup: Have a clear plan to revert any changes made. This includes deleting created files, removing test accounts, and restoring any modified configurations to their original state immediately after the proof is captured.
By focusing on controlled validation, you can effectively test security controls and demonstrate risk without jeopardizing the organization's operational stability.
6. Comprehensive Documentation and Evidence Management
Beyond finding vulnerabilities, a penetration test's true value lies in the quality and integrity of its documentation. Comprehensive documentation and evidence management involve the systematic, real-time recording of all testing activities, methodologies, findings, and proof of concept exploits. This is not an afterthought but an integral part of the testing process, creating an auditable trail that is defensible, repeatable, and actionable for remediation teams.
This meticulous record-keeping is the backbone of a professional engagement. It includes detailed logs, configuration files, screenshots, video captures, and precise, step-by-step procedures to reproduce each discovered vulnerability. In high-stakes environments like banking, a detailed audit trail is non-negotiable for regulatory compliance. Similarly, a healthcare assessment must rigorously document any interaction with systems containing Protected Health Information (PHI) to prove HIPAA compliance and demonstrate that data was not exfiltrated or improperly handled.
Why It's a Top Best Practice
Effective documentation transforms a penetration test from a simple "break-in" exercise into a strategic business tool. It provides undeniable proof of vulnerabilities, quantifies their business impact, and gives developers a clear roadmap for remediation. For legal and compliance officers, this evidence is critical for demonstrating due diligence to auditors, regulators, and stakeholders. Without it, a finding is merely an unverified claim; with it, a finding becomes a powerful catalyst for improving security posture. This is a core component of professional penetration testing best practices.
Implementation Tips
To ensure your documentation is robust and adds maximum value, follow these actionable steps:
- Document in Real-Time: Avoid retrospective documentation. Record commands, observations, and results as they happen. This practice minimizes errors and ensures no critical details are forgotten.
- Use Consistent Naming Conventions: Standardize how you name files, screenshots, and evidence logs (e.g.,
YYYYMMDD_TargetIP_Vulnerability_Evidence01.png). This organization is crucial for efficiently building the final report. - Implement Secure Storage: All testing notes and evidence must be stored securely, using encryption both at rest and in transit. This is especially critical when dealing with sensitive client data or classified government projects.
- Link Technical Details to Business Impact: Don't just list a vulnerability. Document its potential impact in a business context. For example, explain how an SQL injection flaw could lead to a customer data breach, financial loss, and reputational damage.
Building a strong documentation habit is key to elevating the quality of your security assessments. For deeper insights into creating effective records, you can learn more about documentation best practices and how they apply across various technical fields.
7. Professional Reporting and Executive Communication
A penetration test’s value is not in the vulnerabilities found, but in the organization's ability to understand and act upon them. Professional reporting is the bridge between complex technical findings and decisive business action. A poorly communicated report renders the entire engagement ineffective, leaving critical security gaps unaddressed. The final deliverable must be clear, actionable, and tailored to its distinct audiences, from system administrators to the C-suite.
This final phase translates raw technical data into business risk context. The report must provide a high-level executive summary that quantifies risk in financial or operational terms, alongside a detailed technical section for IT teams. For example, a report for a financial services firm must explicitly map a discovered vulnerability to the specific PCI-DSS requirements it violates. Similarly, for a healthcare provider, a finding should be connected directly to potential HIPAA breach risks and patient data exposure. This approach ensures all stakeholders recognize the urgency and impact of the findings.
Why It's a Top Best Practice
Effective communication is the linchpin of a successful security program and is a cornerstone of penetration testing best practices. Executive leadership allocates budget and resources based on their understanding of risk. If a report is overly technical or fails to articulate the business impact, decision-makers cannot prioritize remediation efforts, and the identified vulnerabilities will persist. A professional report demonstrates the ROI of the security investment and drives the necessary cultural and procedural changes to improve the organization's security posture.
Implementation Tips
To create reports that drive action and communicate value, follow these key steps:
- Segment Your Audience: Create two distinct sections in your report. An Executive Summary with business impact analysis, risk ratings, and strategic recommendations, and a Technical Deep-Dive with detailed vulnerability replication steps, logs, and specific code-level fixes for developers.
- Provide Actionable Remediation Guidance: Do not just state a problem; provide a clear solution. Offer step-by-step instructions, links to patches, configuration examples, and both short-term containment and long-term remediation strategies.
- Contextualize Findings with Business Impact: Instead of stating "SQL injection found," rephrase it as "Critical SQL injection vulnerability discovered on the customer portal, potentially exposing all 50,000 customer records and risking a regulatory fine of up to $1.5 million under HIPAA."
- Schedule a Debriefing Session: A report should be a conversation starter, not the final word. Schedule a meeting to walk stakeholders through the findings, answer questions, and ensure the remediation plan is clearly understood and achievable.
Mastering the art of reporting is crucial for turning technical discoveries into tangible security improvements. For a deeper dive into structuring your deliverables, consider these effective report writing techniques to maximize their impact.
8. Continuous Retesting and Remediation Validation
A one-time penetration test provides a valuable snapshot of an organization's security posture at a single point in time, but it is not a "one-and-done" solution. Continuous Retesting and Remediation Validation is the practice of systematically verifying that identified vulnerabilities have been properly fixed and that new security controls are effective. This cyclical process transforms penetration testing from a periodic audit into an integral part of the ongoing security lifecycle.
This best practice involves scheduling follow-up tests specifically targeting previously discovered flaws. The goal is to confirm that remediation efforts were successful and did not inadvertently introduce new weaknesses. It's a critical feedback loop that ensures security gaps are truly closed, not just temporarily patched. Without this validation, an organization may operate under a false sense of security, believing risks have been mitigated when they still persist.
Why It's a Top Best Practice
In dynamic environments like healthcare IT or legal tech, systems and applications are constantly updated. A vulnerability patched today could reappear in the next software release due to overwritten code or configuration changes. For organizations subject to HIPAA or other compliance mandates, demonstrating a robust remediation validation process is evidence of due care and a mature security program. It proves that the organization not only finds but also effectively fixes security flaws, a key differentiator in regulatory audits and a cornerstone of effective penetration testing best practices.
Implementation Tips
To integrate retesting and validation into your security program, follow these actionable steps:
- Schedule Retesting Based on Risk: Prioritize retesting based on the criticality of the original finding. A critical remote code execution vulnerability should be retested within days of remediation, while a low-risk issue might be validated during the next quarterly scan.
- Focus on High-Impact Areas: Direct validation efforts on previously identified high-risk vulnerabilities and the systems that house sensitive data, like patient records or client legal files. This ensures the most critical attack vectors are verifiably secured.
- Track Remediation Trends: Use retesting data to identify patterns. If the same type of vulnerability, such as cross-site scripting, consistently reappears, it points to a systemic issue in developer training or secure coding practices that needs to be addressed at its root.
- Integrate with Continuous Monitoring: Combine targeted retesting with continuous automated security scanning. This creates a powerful, multi-layered approach where automated tools provide broad coverage while manual retesting offers deep validation of critical fixes.
8-Key Penetration Testing Best Practices Comparison
| Aspect | Proper Scope Definition and Authorization | Comprehensive Reconnaissance and Information Gathering | Risk-Based Vulnerability Assessment and Prioritization | Methodical Testing Methodology Following Industry Standards | Safe and Controlled Exploitation Techniques | Comprehensive Documentation and Evidence Management | Professional Reporting and Executive Communication | Continuous Retesting and Remediation Validation |
|---|---|---|---|---|---|---|---|---|
| Implementation Complexity 🔄 | Medium - requires coordination with stakeholders | Medium - involves multiple data sources and careful execution | High - needs business and technical expertise | High - requires training in frameworks | Medium - careful controlled execution needed | Medium - thorough real-time recording needed | High - balancing technical & executive communication | Medium - scheduling and ongoing cycles required |
| Resource Requirements ⚡ | Moderate - time-consuming setup | Moderate to high - extensive data gathering and tools | High - skilled analysts and business stakeholder input | High - trained testers and peer reviews | Moderate - controlled environment and backups | Moderate to high - storage and management of evidence | Moderate to high - skilled writers and visualization tools | Moderate to high - continuous testing resources |
| Expected Outcomes 📊 | ⭐⭐⭐⭐ Clear legal and operational boundaries | ⭐⭐⭐⭐ Comprehensive target intelligence | ⭐⭐⭐⭐⭐ Prioritized, impactful vulnerability focus | ⭐⭐⭐⭐ Consistent, high-quality, repeatable testing | ⭐⭐⭐⭐ Demonstrated impacts with minimal risk | ⭐⭐⭐⭐ Verifiable findings and compliance support | ⭐⭐⭐⭐ Clear, actionable insights for varied audiences | ⭐⭐⭐⭐ Validated remediation and ongoing security improvement |
| Ideal Use Cases 💡 | Legal compliance, regulated industries | Early-stage info gathering for targeted testing | Resource prioritization, aligning security with business | Organizations needing standardization and quality assurance | Environments requiring minimal disruption and proof of concept | Regulated industries, legal, audit, and knowledge transfer | Executive reporting, compliance, investment justification | Organizations practicing continuous security management |
| Key Advantages ⭐ | Prevents legal issues, sets clear expectations | Identifies attack vectors, uncovers hidden assets | Maximizes testing efficiency, aligns risks with business | Ensures comprehensive, structured testing | Minimizes damage risk, proves real impact | Enables reproducibility, supports remediation and audits | Ensures understanding, helps remediation planning | Confirms fixes, identifies new issues, tracks improvements |
From Testing to True Security Resilience
Navigating the complex landscape of cybersecurity requires more than just running a vulnerability scanner; it demands a strategic, methodical, and continuous approach to security validation. The penetration testing best practices detailed throughout this guide, from meticulous scope definition to comprehensive post-test remediation, are not isolated tasks. Instead, they represent interconnected pillars of a mature security program designed to build genuine, measurable resilience against modern threats. By moving beyond a simple "check-the-box" mentality, organizations in sensitive sectors like legal and healthcare can transform their penetration testing efforts from a compliance obligation into a powerful driver of security improvement.
The journey begins with a foundational understanding that a successful test is defined long before any malicious code is simulated. Proper scope definition and authorization ensure that the engagement is targeted, legal, and aligned with business objectives. This initial planning phase, combined with comprehensive reconnaissance, sets the stage for a test that mirrors the tactics of real-world attackers, providing insights that are both relevant and actionable.
Weaving Best Practices into a Cohesive Strategy
The true value of these practices emerges when they are integrated into a cohesive, cyclical strategy. A methodical approach, whether based on NIST, OWASP, or PTES, provides the structured framework necessary for repeatable and reliable results. However, it is the application of risk-based prioritization that translates raw technical findings into meaningful business context.
Consider these key takeaways as you refine your own approach:
- Context is King: A critical vulnerability on a non-essential development server carries less business risk than a medium-level vulnerability on a patient data repository. Prioritizing remediation efforts based on asset criticality and potential impact ensures that resources are allocated where they are needed most.
- Documentation is Your Defense: For legal and healthcare professionals, robust documentation is not optional. It is your proof of due diligence, a critical record for compliance audits, and an essential tool for tracking remediation. Every step, from initial authorization to final remediation validation, must be meticulously recorded.
- Communication Bridges the Gap: The most technically brilliant penetration test is worthless if its findings are not understood by decision-makers. Crafting clear, professional reports with executive summaries that speak to business risk is just as important as the technical exploitation itself.
Mastering these penetration testing best practices is about embedding a culture of proactive security into your organization's DNA. It is about fostering a continuous loop of testing, identifying weaknesses, remediating them, and re-validating your defenses. This iterative process ensures that your security posture is not a static snapshot but a dynamic, evolving shield that adapts to the changing threat landscape.
Beyond the Report: Fostering a Culture of Security
Ultimately, the goal extends beyond the final report. It is about using the intelligence gathered from each test to make informed strategic decisions. This could mean investing in targeted security awareness training for employees, justifying budget for new security technologies, or refining incident response plans based on simulated attack paths. When executed correctly, a penetration test provides a clear, evidence-based roadmap for strengthening your defenses and protecting your most sensitive assets.
By embracing this holistic view, you elevate your security program from a reactive function to a strategic business enabler. You build trust with clients, patients, and regulators by demonstrating a tangible commitment to security and compliance. This commitment transforms penetration testing from a periodic audit into an engine for continuous improvement, building a security posture that is not just compliant, but genuinely resilient.
Managing the sensitive reports and detailed evidence from a penetration test requires a secure and compliant platform. Whisperit provides an end-to-end encrypted solution perfect for securely documenting findings, collaborating on remediation, and maintaining a clear audit trail. Ensure your entire testing lifecycle is protected by visiting Whisperit to see how we can secure your most critical security data.