How to Conduct a Risk Assessment: Your Expert Guide
The Risk Assessment Mindset: Beyond Basic Compliance
Conducting a risk assessment is more than just a checklist for compliance; it's a vital strategic tool. It's about proactively identifying potential threats and vulnerabilities that could disrupt your operations, damage your reputation, or impact your bottom line. This proactive approach helps organizations build resilience and stay ahead of the competition in an uncertain world. Organizations that embrace risk assessment gain a strategic advantage, enabling them to navigate challenges and achieve their goals.
Shifting From Reactive to Proactive
Many organizations take a reactive approach to risk assessment, often prompted by incidents or audit findings. However, effective risk management requires a proactive mindset. This means anticipating potential threats and vulnerabilities, rather than reacting to past events. Imagine a company that implements security measures only after a data breach. This reactive approach is costly and damaging. A proactive risk assessment could have identified and addressed those vulnerabilities beforehand. For a comprehensive strategy, consider established frameworks for Software Development Risk Management.
Integrating Risk Into Decision-Making
Risk-mature organizations go beyond simply conducting assessments; they integrate the findings into decision-making processes at all levels. This ensures that risk considerations are factored into strategic planning, project management, and daily operations. This integration cultivates a risk-aware culture where everyone understands their role in managing risk. It also empowers organizations to make informed decisions that balance potential rewards with potential downsides.
Understanding the Evolving Risk Landscape
Conducting a risk assessment requires understanding the current risk landscape, which is becoming increasingly complex. The Global Risks Report 2025 highlights that state-based armed conflict is a major risk, with 23% of respondents indicating it as a potential global crisis. This is followed by extreme weather events at 14% and geo-economic confrontation at 8%. Identifying these top-tier risks is critical for a comprehensive risk assessment. This involves analyzing both short-term and long-term threats, such as cybersecurity risks and the impacts of climate change. Effective risk management necessitates a forward-thinking approach. Engaging with stakeholders and leveraging insights from global experts are essential for developing actionable strategies. Learn more about these risks here. This emphasizes the need for a comprehensive and dynamic approach to risk assessment that goes beyond compliance and actively shapes organizational strategy.
Step 1: Map Your Critical Assets and Establish Context

The foundation of any robust risk assessment lies in understanding what needs protecting. This begins with identifying your critical assets: the resources, processes, and information vital to your organization's operations and overall success. Simply compiling a list isn't enough; understanding the intrinsic value of these assets is paramount.
Identifying and Categorizing Your Assets
Begin by creating a thorough inventory of your assets. This could include tangible assets such as equipment and physical locations, digital assets like sensitive data and proprietary software, and even intangible assets such as brand reputation and public perception. Once compiled, categorize these assets according to their criticality. A straightforward approach uses a high, medium, or low criticality scale based on the asset's potential impact on business operations, financial stability, legal and regulatory compliance, and overall reputation.
Prioritizing Assets Based on Value
It's important to recognize that not all assets are equal. Some hold significantly greater value and require stronger protective measures than others. For instance, sensitive customer data is undoubtedly a higher priority than standard office furniture. Prioritizing based on value focuses your resources on safeguarding the most critical components of your business. For a deeper dive into asset prioritization, compliance risk assessment strategies from Blackbird offer a wealth of information.
Establishing the Context for Your Assessment
With your critical assets identified, the next step is establishing the context for your risk assessment. This involves defining the scope of the assessment, pinpointing relevant regulations and industry standards, and outlining your organization's acceptable level of risk, often referred to as risk appetite. This ensures alignment between your assessment and broader business objectives. This also allows you to communicate risk findings in a language that resonates with executive leadership. Framing your assessment within the context of organizational goals and priorities makes it easier for decision-makers to grasp the importance of your efforts and allocate resources effectively.
To illustrate, if your organization is prioritizing expansion into new markets, your risk assessment should focus on the potential risks tied to that expansion. This direct connection between risk management and strategic objectives enhances the value and impact of your assessment. For a more structured approach, consider exploring this resource on How to master the risk assessment matrix. Additionally, the same resource, How to master the risk assessment matrix, provides valuable insights into creating and utilizing a risk assessment matrix effectively.
To help categorize and prioritize your assets effectively, consider the following framework:
Asset Classification Matrix
A framework for categorizing and prioritizing organizational assets based on their value and criticality
| Asset Category | Examples | Value Considerations | Criticality Level |
|---|---|---|---|
| Data | Customer data, financial records, intellectual property | Confidentiality, integrity, availability, legal and regulatory compliance | High |
| Applications | Customer relationship management (CRM) systems, enterprise resource planning (ERP) systems, email servers | Business operations, customer service, financial management | High |
| Infrastructure | Servers, network devices, workstations, power supplies | Business continuity, system availability, data security | Medium |
| Facilities | Office buildings, data centers, warehouses | Physical security, safety, environmental impact | Medium |
| Personnel | Employees, contractors, consultants | Knowledge, skills, experience, reputation | High |
| Reputation | Brand image, public perception, customer trust | Customer loyalty, market share, financial performance | High |
This matrix provides a starting point for classifying your organization's assets. Remember to tailor it to your specific circumstances and regularly review and update it as needed. By clearly categorizing and prioritizing assets, your organization can make more informed decisions regarding resource allocation for protection and mitigation efforts.
Step 2: Identify and Analyze Threats That Actually Matter
After mapping your critical assets, the next crucial step in conducting a risk assessment involves identifying and analyzing the threats that pose a genuine risk to those assets. This goes beyond simply brainstorming hypothetical scenarios; it requires a structured approach to threat intelligence. This means understanding both the likelihood of a threat occurring and the potential impact it could have.
Building a Threat Intelligence Framework
A robust threat intelligence framework is essential for capturing both emerging and established risks. This framework should incorporate various sources of information, including industry reports, threat databases, and even open-source intelligence. You might be interested in: How to conduct a third-party risk assessment. For example, a financial institution might monitor reports on new phishing techniques or emerging malware targeting the financial sector.
This proactive approach allows organizations to anticipate and prepare for threats before they materialize.
Threat Horizon Scanning and Quantification
Effective threat horizon scanning involves looking beyond immediate threats to identify potential future risks. This doesn't mean getting bogged down in every hypothetical scenario. Instead, focus on sector-specific threat patterns and broader global trends. Statistically, the Global Risks Report 2025 highlights a decline in global optimism, with heightened tensions across various domains, including geopolitical, environmental, and economic.
This is evident in the increasing frequency and severity of climate-related events impacting economies globally. When conducting a risk assessment, incorporating these broader trends and their potential impact is crucial. Find more detailed statistics here. Threat quantification is essential for translating nebulous concerns into measurable business impact.
This involves assigning numerical values to the likelihood and potential impact of each threat. This allows for a more objective assessment of risk and helps prioritize mitigation efforts.
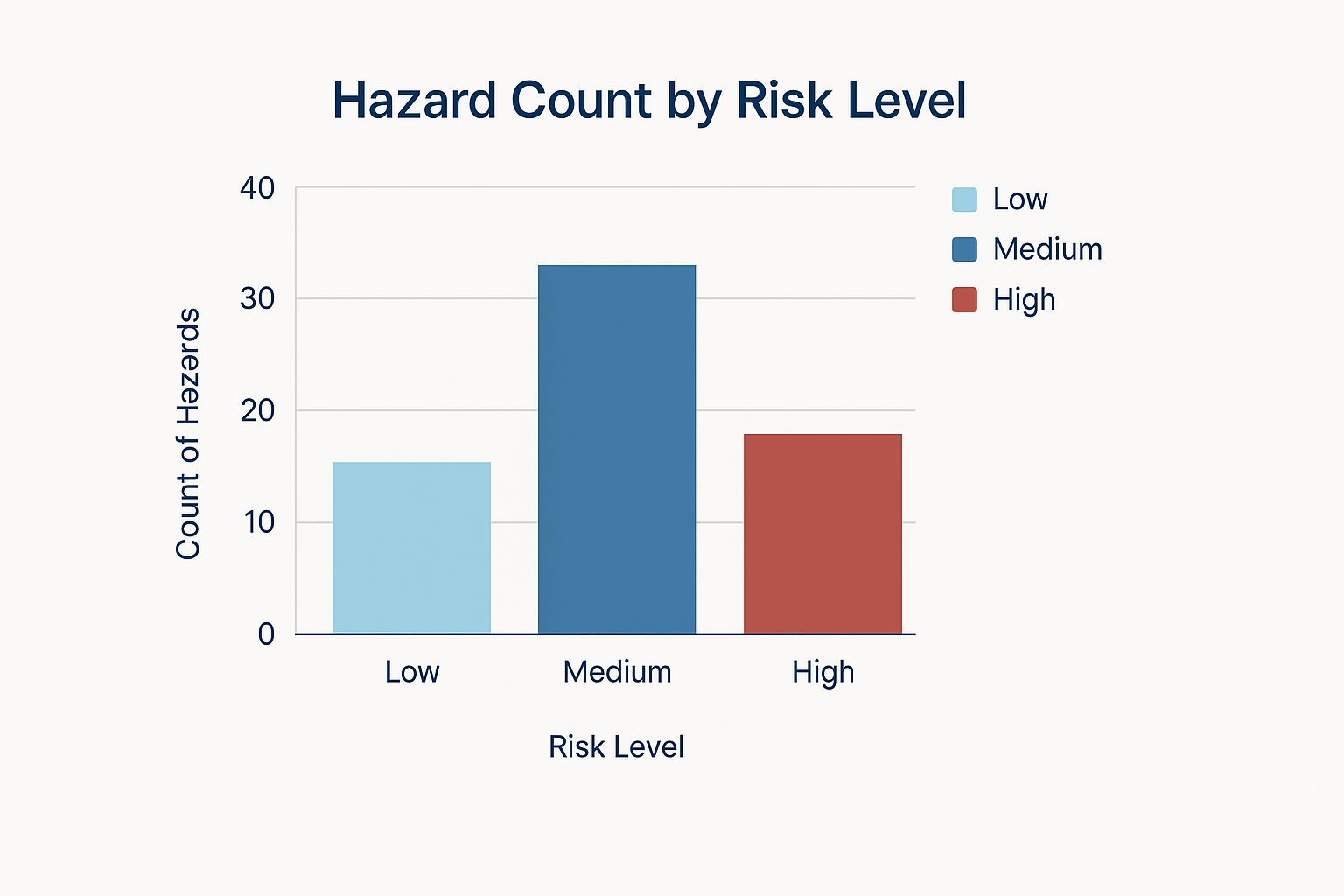
The infographic above visualizes the count of hazards categorized by risk level (low, medium, and high). As the infographic clearly shows, while medium-level risks are the most frequent, a significant number of hazards are categorized as high risk, demanding immediate attention. This emphasizes the need to prioritize these high-risk hazards during mitigation and response planning. To further illustrate this process, let's examine a potential threat probability and impact assessment.
The following table provides a framework for evaluating identified threats based on their likelihood of occurrence and potential impact severity.
| Threat Category | Likelihood Rating | Impact Rating | Risk Score | Priority Level |
|---|---|---|---|---|
| Data Breach | High | High | Critical | 1 |
| Denial of Service Attack | Medium | High | High | 2 |
| Phishing Attack | High | Medium | Medium | 3 |
| Insider Threat | Low | High | Medium | 4 |
| Natural Disaster | Low | Low | Low | 5 |
This table demonstrates how assigning numerical values to likelihood and impact allows us to calculate a risk score and prioritize threats accordingly. This structured approach allows for a more objective assessment of risk and helps focus mitigation efforts where they are most needed.
Documenting Threats Effectively
Finally, documenting threats in a structured and actionable way is crucial. This goes beyond simply creating a list of potential threats. The documentation should include a detailed description of each threat, its potential impact on critical assets, the likelihood of occurrence, and the assigned risk level. This documentation serves as a valuable resource for developing and implementing effective risk responses.
This structured approach ensures that the risk assessment process is thorough, consistent, and provides a clear basis for decision-making. This also facilitates communication with stakeholders and helps to ensure that resources are allocated effectively to address the most significant threats.
Step 3: Uncover Hidden Vulnerabilities Before They’re Exploited
Identifying threats is only half the battle. To effectively conduct a risk assessment, you must also understand your vulnerabilities: the weaknesses that threats can exploit. The most dangerous vulnerabilities are often hidden, lurking beneath the surface of seemingly secure systems. This section explores how to proactively uncover these weaknesses before they're exploited.
Going Beyond the Obvious
Many organizations focus on obvious vulnerabilities, such as outdated software or weak passwords. However, sophisticated threats often target more subtle control gaps.
For example, a poorly defined access control policy could allow unauthorized individuals to access sensitive data, even if passwords are strong. Or, a lack of security awareness training among employees can make them susceptible to phishing attacks. Identifying these hidden vulnerabilities requires a deeper understanding of your organization's processes and systems.
Practical Vulnerability Assessment Techniques
Various techniques can be employed to assess vulnerabilities, ranging from technical scans to manual reviews. Penetration testing, for instance, simulates real-world attacks to identify weaknesses in your security defenses. Vulnerability scanners automate the process of checking for known vulnerabilities in software and systems.
However, these automated methods shouldn't replace human analysis. Manual reviews of policies, procedures, and system configurations are crucial for uncovering subtle control gaps that automated tools might miss. For example, a tabletop exercise, where team members walk through a simulated incident, can reveal surprising security gaps in incident response plans. You might be interested in: How to master data security and compliance.
Continuous Vulnerability Discovery
Leading organizations don't just conduct point-in-time vulnerability assessments. They establish ongoing vulnerability discovery programs that continuously strengthen their defenses. This continuous approach recognizes that new vulnerabilities are constantly emerging.
Regular security awareness training, for instance, can help employees recognize and report suspicious activity, mitigating the risk of phishing and other social engineering attacks. By constantly searching for and addressing vulnerabilities, these organizations maintain a strong security posture.
Mapping Vulnerabilities to Threats
Finally, it's crucial to map identified vulnerabilities to specific threats. This helps prioritize remediation efforts. For instance, if a vulnerability exists that could allow an attacker to gain access to sensitive customer data, and a credible threat of data breaches exists, this combination represents a high-priority risk.
Conversely, a vulnerability that only impacts a non-critical system and is tied to a low-probability threat can be given lower priority. This process of mapping vulnerabilities to threats provides a clear framework for allocating resources and focusing on the most significant risks. By prioritizing remediation efforts based on the severity of the risk, organizations can maximize their impact and ensure that the most critical vulnerabilities are addressed first. This approach ensures that resources are used effectively and that the organization's security posture is continuously improved.
Step 4: Transform Risk Data Into Actionable Intelligence

Raw risk data, without proper analysis, is just noise. This step focuses on converting the data gathered into actionable insights to inform smart decision-making. This involves both qualitative and quantitative analysis, building a comprehensive understanding of your organization's unique risk profile.
Calculating Meaningful Risk Scores
Risk scoring, assigning numerical values to risks, allows for objective comparison and prioritization. This typically involves assessing the likelihood of a threat exploiting a vulnerability and the potential impact if that happens. A high-likelihood, high-impact risk gets a higher score than a low-likelihood, low-impact one.
These scores should reflect your organization's specific risk appetite and business context. A high-risk score for one organization might be medium or even low for another.
Visualizing Risk Relationships
Data visualization transforms complex risk relationships into digestible formats. Charts, graphs, and heat maps can highlight risk concentrations and patterns easily missed when reviewing individual risks. This clear visual presentation simplifies communicating risk information to stakeholders and builds consensus for mitigation strategies.
Determining Acceptable Risk Thresholds
Organizations must establish risk thresholds: the level of risk they're willing to accept. These thresholds should be based on industry standards, regulatory requirements, organizational maturity, and strategic objectives. A startup, for example, might have a higher risk tolerance than a mature corporation. These thresholds act as a benchmark against which risk scores can be compared to determine appropriate responses.
Aggregating Risks for a Systemic View
Analyzing individual risks is crucial, but incomplete. Risk aggregation combines risks to identify patterns and concentrations not apparent when looking at threats individually. This reveals systemic vulnerabilities requiring strategic, organization-wide responses. For example, risk aggregation might reveal multiple seemingly unrelated threats depending on a single critical system, highlighting its importance. You might be interested in: How to master information security policies.
From Intelligence to Action
Transforming raw data into actionable intelligence empowers informed decisions about risk responses. Understanding the relative importance of different risks allows organizations to prioritize mitigation efforts and allocate resources effectively. This ensures the most significant risks are addressed first, maximizing the impact of risk management activities. This data-driven approach shifts risk management from reactive to proactive, enabling informed decisions that contribute to resilience and success.
Step 5: Design Risk Strategies That Actually Get Implemented

After identifying and analyzing your risks, the next step in conducting a risk assessment is developing effective risk strategies. This involves choosing the right response and creating actionable plans to address each risk. A well-designed risk strategy isn't just a theoretical document; it's a practical roadmap for taking action.
Choosing The Right Risk Strategy
There are four main risk strategies: acceptance, avoidance, transfer, and mitigation. Risk acceptance means acknowledging the risk but choosing not to take action. This is suitable for low-probability, low-impact risks. Risk avoidance involves eliminating the risk entirely, perhaps by discontinuing a specific activity or process.
Risk transfer shifts the risk to a third party, such as through an insurance policy. Finally, risk mitigation involves reducing the likelihood or impact of the risk. This is the most frequently used risk strategy. The best strategy depends on the specific risk, your organization's risk appetite, and the resources available.
Creating SMART Risk Action Plans
Effective risk strategies need SMART action plans. SMART stands for Specific, Measurable, Achievable, Relevant, and Time-bound. A SMART action plan clearly defines the actions, assigns responsibility, outlines required resources, and sets completion deadlines.
For example, mitigating the risk of a data breach might involve implementing multi-factor authentication, regular security awareness training, and an incident response plan. Each action should have a specific deadline and assigned responsibility.
Overcoming Implementation Challenges
Putting risk strategies into practice can be difficult. Common obstacles include resource constraints, competing priorities, and stakeholder resistance. To overcome these challenges, secure buy-in from key stakeholders, communicate the benefits of the strategies clearly, and dedicate sufficient resources.
For instance, if a new security policy faces resistance, demonstrating its effectiveness in protecting sensitive data can improve acceptance. Breaking down large projects into smaller, manageable tasks can help overcome resource limitations and maintain progress.
Documenting Risk Treatments
Thorough documentation is crucial for effective risk management. Your documentation should clearly outline the chosen risk strategies, the reasons behind them, the related action plans, and any metrics for measuring success. This documentation not only fulfills governance requirements but also provides a valuable tool for future risk assessments.
This documentation needs regular review and updates to reflect changes in the risk environment. You might find this helpful: How to create a robust audit trail. This ensures your risk management program stays relevant and effective against evolving threats. Documenting risk treatments creates a record of your decisions and actions, enabling continuous improvement and demonstrating due diligence.
Step 6: Build a Living Risk Program That Evolves With Threats
A risk assessment isn't a one-time event; it's an ongoing process. It must adapt to the constantly shifting landscape of potential threats. This means building a living risk program—one that continually strengthens your defenses. This section explores how leading organizations create risk programs that are both sustainable and adaptable to emerging threats.
Effective Risk Documentation and Communication
Clear, concise documentation is key for effective communication about risk. Different stakeholders need different types of information. Technical teams, for example, require detailed information about specific vulnerabilities and how to mitigate them. Executive leadership, on the other hand, needs high-level summaries of the key risks and their potential impact on the business.
Think of it this way: a technical document might detail specific vulnerabilities within a web application. An executive summary, however, would focus on the potential financial and reputational fallout from a data breach. Effective documentation makes sure everyone has the information they need to understand and manage risk. For more detailed information on proper documentation, take a look at this guide on How to master audit trail best practices.
Establishing Review Cycles
Regular reviews are crucial to keeping your risk program up-to-date. The frequency of reviews should balance thoroughness and efficiency. An annual review might be sufficient for some organizations. Others, operating in more dynamic environments, might require quarterly or even monthly reviews.
It’s also vital to establish triggers for risk reassessment that go beyond the calendar. These triggers might include significant organizational changes, like a merger or acquisition. They could also be tied to incident responses, such as a data breach, or the emergence of new threat indicators like a new malware strain.
Integrating Risk Assessment Into Organizational Culture
Mature organizations weave risk assessment into the fabric of their culture. This shifts the focus from simple compliance to a true competitive advantage. When risk considerations become part of daily decision-making, from project planning to resource allocation, the organization becomes inherently more resilient.
This cultural shift requires training and awareness programs to educate employees about risk management principles and their role in protecting organizational assets. It fosters a sense of shared responsibility, making risk management everyone's job.
Measuring and Demonstrating Value
Demonstrating the value of your risk program is essential for securing ongoing support and resources. This means using clear metrics to measure the effectiveness of your risk management efforts. These metrics could include the number of vulnerabilities identified and remediated, a reduction in the likelihood or impact of specific risks, or even cost savings from avoided security incidents.
Regularly reporting these metrics to leadership demonstrates the tangible benefits of the program and justifies continued investment. This data-driven approach elevates risk management from a cost center to a strategic asset, showcasing its value and making it integral to the organization's success.
Leveraging AI-Powered Tools
Modern risk assessment increasingly utilizes AI-powered tools. These platforms automate many aspects of the process, from gathering threat intelligence to scanning for vulnerabilities. AI can analyze vast amounts of data, identifying patterns and trends that humans might miss.
This allows risk professionals to focus on higher-level tasks like strategy development and communication. It's crucial to remember, though, that AI is a tool, not a replacement for human expertise.
Building a Sustainable Risk Management Program
Building a sustainable risk management program is an ongoing journey. It requires commitment at every level of the organization. By incorporating these steps, organizations can create a dynamic risk management framework that continually strengthens their defenses. A living risk program not only protects against threats, but also allows for innovation and growth by providing a structured approach to managing uncertainty.
Ready to streamline your documentation and enhance your risk management processes? Whisperit, an AI-powered dictation and text editing platform, can help you create, manage, and communicate risk-related information efficiently and securely. Visit Whisperit today to learn more.