Secure HIPAA Compliant Document Sharing for Healthcare
The Hidden Costs of Getting Document Sharing Wrong
Let's talk about something that gives healthcare administrators nightmares: the real financial fallout from HIPAA violations. I've talked with IT directors who've seen organizations get slammed with six-figure fines just because someone sent a patient file through regular email. These fines aren't pocket change; they can be devastating, especially for smaller practices. And beyond the obvious penalties? Hidden costs that can really hurt.
Think about your reputation, for example. A HIPAA violation is a trust-buster. It makes it tough to attract new patients and keep the ones you have. Bad news spreads like wildfire, and the negative press can stick around for a long time. Then there are the legal fees. Even if you avoid the maximum penalties, lawyer bills add up fast. Responding to investigations, hiring legal counsel, and dealing with the complicated regulations is pricey.
And let's not forget the cost of breach notification. HIPAA says you have to notify affected individuals, the Department of Health and Human Services (HHS), and maybe even the media if there's a breach. Think postage, phone calls, and maybe even credit monitoring services for patients. It gets expensive quickly, especially if the breach is large. HIPAA compliance in document sharing has become mission-critical, especially with the move to digital. Regular file-sharing services like Dropbox and Google Drive aren't automatically HIPAA-compliant. You need extra precautions, like a Business Associate Agreement (BAA). This is key, since non-compliance fines can range from $100 to $50,000 per violation, depending on how bad it is. The rise of remote work and telehealth just makes secure, HIPAA-compliant document sharing even more important for protecting patient health information (PHI). The demand for these solutions is still growing, with new, secure options popping up all the time to address the risks of old-school document sharing. Discover more insights on HIPAA compliant document sharing.
Real-World Consequences
I've heard some real horror stories about simple document sharing mistakes leading to huge problems. One doctor emailed patient info to a colleague from a personal email account – big fine, and mandatory retraining for the whole staff. Another organization used a file-sharing service without a BAA, leaving patient data exposed and opening themselves up to major legal trouble. These things happen more than you think.
Warning Signs Your Organization Needs Attention
Remote work and telehealth have changed everything, creating new vulnerabilities. Are your employees using personal devices to access or share PHI? Are you sure your file-sharing practices are secure? Do you have clear policies and procedures, and are they up to date? These are crucial questions. If you’re not sure about the answers, it’s time to take a hard look. Ignoring this can cost you way more than investing in a solid, HIPAA-compliant document sharing system.
Building Security That Actually Protects Your Data
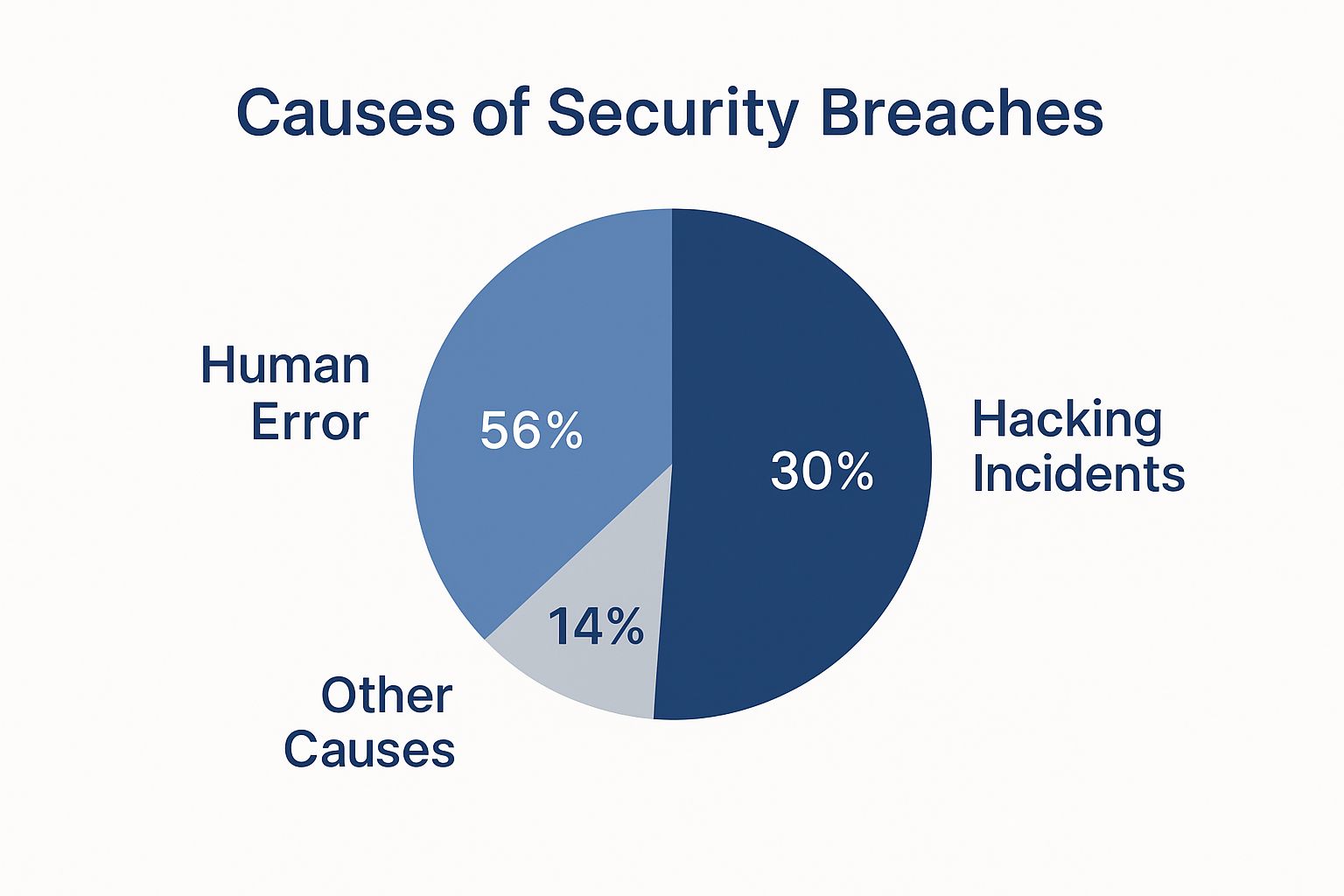
The pie chart above throws some interesting numbers at us. 56% of data breaches come down to human error. Hacking sits at 30%, with the remaining 14% attributed to other causes. This makes one thing crystal clear: even with top-notch tech, human error can really throw a wrench in the works. So, how do you build a security system that's both airtight and user-friendly?
Encryption and Access Controls: The Foundation of Security
Let's talk encryption. It's easy to get lost in the weeds, but honestly, you don't need to be a cryptography expert. Focus on two key concepts: data-at-rest encryption (protecting stored data) and data-in-transit encryption (protecting data as it moves). Think of it this way: you lock your filing cabinet (data-at-rest) and you send sensitive documents by secure courier (data-in-transit). In the digital world, AES-256 encryption is the gold standard. Look for solutions that offer it.
Access controls are your next line of defense. The principle of least privilege is your guiding star here. Give people access only to what they absolutely need. It's like giving staff keys to specific rooms, not the entire building. This keeps damage contained if a breach happens, plus it simplifies management.
Now, to give you a clearer picture of how to build a secure system, let's look at a comparison table. This breaks down essential security features and what you need to consider for proper HIPAA compliance.
Essential Security Features Comparison
| Security Feature | Minimum Requirement | Best Practice | Audit Consideration |
|---|---|---|---|
| Encryption | Data at rest and in transit with a strong cipher | AES-256 encryption | Verify encryption implementation and key management practices |
| Access Controls | Role-based access control | Principle of least privilege, multi-factor authentication | Review access logs regularly for suspicious activity |
| Audit Trails | Logging of access, modifications, and deletions | Real-time alerts for anomalous behavior | Ensure audit trails are tamper-proof and regularly reviewed |
This table lays out a clear path to building a secure framework. Remember, best practices are there to offer maximum protection, so aim high!
Auditing: Your Proof of Compliance
Audit trails are your security cameras in the digital realm. They record who accessed what, when, and from where. This isn't just good practice—it's essential for proving HIPAA compliance and tracking down anything fishy. Don't just collect these logs; actually use them. Set up alerts for unusual access patterns, like a staff member suddenly downloading massive amounts of data they've never touched before. Catching these red flags early is crucial.
Speaking of catching things early, consider this: from 2018 to 2023, hacking incidents shot up by a whopping 239%, according to Dialog Health’s HIPAA statistics. This highlights the need for robust security measures like zero-trust frameworks in your file-sharing systems. It's no wonder the secure file transfer market is predicted to reach $3.63 billion by 2029. This heightened focus on data security is a trend you definitely want to be ahead of. Learn more about security statistics. You might also find our insights on call center compliance useful.
Validating and Testing: Don't Wait for a Crisis
Don't just hope your system is secure. Put it to the test. Regular penetration testing simulates real-world attacks, exposing any vulnerabilities before they become a real problem. Think of it as a fire drill for your data. Finding weaknesses in a controlled setting is much better than discovering them during a breach. For further insights, check out our article on document management security.
And finally, let's not forget the human element. Even the best tech fails if your team doesn't know how to use it. Regular training reinforces best practices and helps prevent those human errors we discussed earlier. Invest in your team, and they'll become your strongest asset in maintaining security.
Choosing Vendors Without Getting Burned by Marketing Hype

Let's talk vendor selection for HIPAA-compliant document sharing. I've been there, seen the slick demos, heard the empty promises. Trust me, it's easy to get seduced by marketing hype, only to discover your "HIPAA-compliant" solution is anything but. Let’s avoid that expensive mistake, shall we?
Beyond the Buzzwords: Evaluating Real Compliance
First, ditch the buzzwords. "Secure" and "compliant" are practically meaningless without proof. Ask for HIPAA compliance documentation, specifically their Business Associate Agreement (BAA). Don't just skim it—read it. Does it clearly define their responsibilities and your protections in case of a breach? A vague BAA is a massive red flag.
Then, dig into the nitty-gritty of their encryption. Are they using industry-standard AES-256 encryption for data both at rest and in transit? What about their key management system—is it robust? These aren't just technical details; they're the foundation of your security. Weak encryption leaves you vulnerable. Speaking of security best practices, fortifying your Jira instance is also worth considering. Here’s a helpful resource on secure Jira API authentication: 3 Ways To Promote Secure Jira Api Authentication For Your Users.
Next up: access controls. Can you implement role-based access to ensure the principle of least privilege? Is multi-factor authentication an option? You need granular control over who sees what.
Finally, don't overlook audit trails. A solid system should track who accessed what, when, and from where. You need this data for compliance audits and breach investigations. It’s not a luxury; it’s a necessity. Broadening your understanding of vendor risk management can also be incredibly beneficial.
Asking the Right Questions: Avoiding Vendor Traps
To help you navigate this process, I've put together a checklist based on my own experience:
Here’s a checklist to help you evaluate potential vendors:
Vendor Evaluation Checklist
| Evaluation Criteria | Must-Have | Nice-to-Have | Red Flags |
|---|---|---|---|
| BAA | Clearly outlines responsibilities and liabilities | Indemnification clause | Vague language, reluctance to sign |
| Encryption | AES-256 encryption for data at rest and in transit | Hardware encryption | Weak encryption standards |
| Access Controls | Role-based access control | Multi-factor authentication | Limited access control options |
| Audit Trails | Detailed logs of user activity | Automated reporting | Inability to generate audit reports |
Choosing a vendor is like choosing a business partner. You're entrusting them with sensitive data and your organization's reputation. Take your time. Ask the tough questions. Don't be afraid to walk away if something feels off. A little due diligence upfront can save you a world of pain (and expense) later on.
Creating Policies Your Team Will Actually Use
Let's be honest: even the most impressive, HIPAA-compliant document sharing platform won't do much if your team avoids using it. I've seen this happen firsthand. Staff revert to using personal email because the "secure" system is so cumbersome that it makes their jobs harder. That completely negates the point, doesn't it?
Balancing Security and Workflow
Good HIPAA-compliant document sharing policies find a sweet spot between actual security needs and the everyday realities of healthcare work. They shouldn't be a laundry list of "don'ts." Imagine a doctor needing to quickly share test results with a specialist for urgent care. A system requiring multiple approvals and logins could seriously hinder patient care.
The organizations that really get this right build policies people want to follow. This means understanding your team's workflow. What are their biggest pain points with current systems? Where are the bottlenecks? For more on streamlining, you might find our guide on document management best practices helpful.
Addressing Common Policy Failures
One common mistake is creating policies in isolation. Don’t just hand down rules from on high. Get everyone involved – doctors, nurses, administrative staff – everyone who will use the system. This builds buy-in and helps you uncover practical challenges before they turn into compliance headaches.
Another trap is focusing only on external threats. Internal issues matter too. Remember, 56% of breaches are due to human error. Your policies need to address this head-on. Offer clear, simple guidelines, not pages of legal jargon. Focus on education, not punishment. Explain why certain actions are risky, not just that they're forbidden. This creates a culture of security, where compliance becomes everyone's responsibility.
Training That Sticks
Your carefully crafted policies are useless without effective training. A one-time presentation just won't cut it. Make training ongoing and interesting. Use real-world examples, case studies, even gamification. Regular refreshers help keep security top-of-mind and reinforce good habits.
Addressing Frustration, Not Malice
Most compliance violations aren’t malicious. They happen because people are frustrated with difficult systems. If your system is a pain to use, people will find workarounds, even if they know the risks. Fix the root of the problem by focusing on user-friendliness. Streamline workflows, simplify processes, and offer good support. When the secure option is the easiest option, that’s what people will use.
Building a Culture of Compliance
In the end, successful HIPAA-compliant document sharing depends on building a culture of compliance. It's about making security everyone's job. It's about creating policies that are practical, training that’s engaging, and systems that are easy to use. Do that, and you're not just checking boxes; you're building a system that actually protects patient data and lets your team work efficiently and securely.
Setting Up Monitoring That Catches Problems Early

This screenshot from Wikipedia's HIPAA page reminds us how broad HIPAA compliance really is. It covers everything from privacy and security to enforcement. And when you’re dealing with document sharing, a truly comprehensive approach is non-negotiable. Effective monitoring? That’s a core piece of the puzzle. I’ve seen too many organizations think they’ve nailed HIPAA-compliant document sharing, only to get tripped up during an audit. Let's avoid that, shall we?
Proactive Monitoring: Spotting Problems Before They Escalate
Picture this: your monitoring system pings you about unusual activity. A staff member is poking around in files they don’t normally access. You dig a little deeper and find out they were just covering for a colleague. Harmless, right? Not quite. That seemingly innocent action is a potential HIPAA violation waiting to happen.
Proactive monitoring isn't about playing "gotcha!" It's about uncovering vulnerabilities before they become real problems. Think of it as preventative care for your data security. By keeping tabs on document access, user behavior, and setting up smart alerts, you’re catching the small stuff before it snowballs into a major (and expensive) headache. It’s all about shifting from reactive damage control to proactive problem-solving.
Audit Trails: Your Digital Detective
Audit trails are your digital detectives. They tell you who accessed what file, when they accessed it, and where they accessed it from. But here's the catch: a mountain of logs is useless if nobody's analyzing them. I've seen organizations drowning in data, completely missing critical red flags because their logs were too overwhelming.
The key is to make your audit trails work for you. Focus on the metrics that truly matter for ongoing compliance. Think about who is accessing your most sensitive data, how often files are downloaded, and whether any of this is happening outside of normal business hours. Those are the clues you need to follow.
Intelligent Alerts: No More Alert Fatigue
Let's be honest, alert fatigue is real. If your IT team is constantly bombarded with alerts, they're going to start tuning them out. And that's a recipe for disaster. The solution? Intelligent alerts. These focus on truly suspicious activity, not just any old access. Is someone downloading thousands of files at 3:00 AM? Yeah, that needs immediate attention. Someone accessing a file they need for their daily tasks? Probably not a big deal.
The best way to start is by defining what "suspicious" looks like for your organization. What's normal for a large hospital might be a huge red flag for a small clinic. Refine your alerts over time to strike the right balance between being vigilant and keeping your team sane. You want to catch the problems without drowning in noise. For a deeper dive into audit prep, check out our security audit checklist: Learn more in our article about a Security Audit Checklist.
Internal and External Audits: Be Prepared
Regular internal audits aren’t just a box to check; they're your practice run for external audits. They give you a chance to spot weaknesses and fix them before an external auditor finds them. Think of it as a dress rehearsal before the big performance.
For both internal and external audits, clear documentation is your best friend. Auditors don’t just want to see that you have systems; they want proof that those systems actually work. This means having everything from your policies and procedures to your training materials and incident response plans readily accessible. Being prepared demonstrates that you’re serious about HIPAA-compliant document sharing.
By proactively monitoring, using intelligent alerts, and conducting regular audits, you're building a culture of security. You're not just reacting to problems; you're anticipating them. This not only saves you from potential HIPAA headaches but also builds trust with your patients. They know their data is safe with you, and that’s priceless.
Testing Your System Before You Need It Most
I've seen it happen firsthand: a healthcare facility faces a real emergency, only to discover their backup systems have gone belly up. It’s not pretty. The same scenario plays out with HIPAA-compliant document sharing systems that haven't been properly tested. Trust me, you don't want to uncover vulnerabilities during an actual breach or audit. That’s why testing is absolutely critical.
Penetration Testing: Simulating Real-World Attacks
Picture this: someone’s trying to break into your system. What are their tactics? Penetration testing simulates these real-world attacks. Think of it like an ethical hacking exercise. A qualified security expert probes your system, searching for weaknesses just like a real attacker would. This can reveal vulnerabilities you might have missed. For example, they might try to crack your authentication by bypassing logins or exploiting weak passwords. They could attempt to intercept data in transit, or even access stored data by leveraging encryption flaws.
Validation Techniques: Checking Your Compliance
While penetration testing mimics external threats, validation zeroes in on internal compliance. Are your document sharing processes truly HIPAA compliant? This means rigorously examining every facet of your system. Is your encryption up to snuff? Are access controls correctly implemented and enforced? Is every single action logged in your audit trails? A practical example would be testing user access by creating different user roles with varying permissions. Then, you verify that each user can only access the information they're authorized to see. Another example: validate audit trails by performing actions within the system—like uploading, downloading, and deleting a document—then checking the logs to ensure everything is accurately recorded, including timestamps, user IDs, and specific actions taken.
Common Testing Oversights and How to Avoid Them
One common pitfall is testing in a “perfect world” scenario. Real-world systems experience bumps in the road. Introduce some stress. What happens if your server goes down? What if user activity suddenly spikes? How does your system cope? These tests uncover hidden vulnerabilities that wouldn't surface under normal conditions. Another frequent oversight is neglecting to test all access points. Consider mobile devices, third-party applications, and even employee remote access. Every entry point is a potential vulnerability.
Practical Examples of Successful Validation
I once worked with an organization that took a multi-layered validation approach. They not only conducted penetration testing and internal validation, but they also brought in external auditors for a mock audit. This highlighted gaps in their documentation and procedures. Another organization I know built automated validation checks into their software development lifecycle. Each system modification triggered automated tests to ensure no new security vulnerabilities were introduced. Smart, right?
Ongoing Validation: Staying Ahead of the Curve
Technology evolves, and so do threats. Security isn't a one-and-done deal; it's a continuous process. Regularly review and update your security policies. Conduct periodic penetration testing and validation exercises. Stay up-to-date on the latest vulnerabilities and emerging threats. This proactive approach protects your system as it grows and changes, ensuring your HIPAA-compliant document sharing practices remain effective. This vigilance is essential in the constantly evolving cybersecurity landscape.
Your Roadmap to Sustainable Compliance Success

This isn’t about slapping a band-aid on your document sharing and calling it a day. It’s about creating a HIPAA-compliant system that's built to last. Think long-term protection that can flex and adapt as your organization grows and the regulations inevitably change. Let's map out how to make that happen.
Prioritize and Plan: Starting Strong
First, honestly assess your vulnerabilities. Where are your current document sharing practices most at risk? Are employees still using unencrypted email? Does your file storage system have adequate access controls? I’ve seen organizations try to overhaul everything at once, and it can quickly become overwhelming. Instead, focus on the areas posing the greatest risk. Pick one area, build a solid foundation, and then expand from there.
Start small, think big.
Milestones and Measurement: Tracking Your Progress
"We're improving security" sounds great, but what does that even mean? Real progress hinges on measurable goals. Define what "better" actually looks like. Maybe it's cutting down on unencrypted email by 50% within three months. Or maybe it’s finally getting that multi-factor authentication (MFA) rolled out for everyone accessing patient records by the end of the year. These concrete milestones keep your team focused and give you a real way to track progress and demonstrate tangible improvement. It also keeps everyone motivated to see those wins along the way!
Troubleshooting and Adaptation: Handling the Inevitable Hiccups
Let's be real, implementing any new system will have its bumps. What if your team pushes back against new procedures? Or what happens if your testing reveals a security gap you didn’t anticipate? You need a plan. Anticipate potential roadblocks, have backup plans, and be ready to adapt. A little flexibility goes a long way. Here’s a resource I’ve found useful in the past: data privacy compliance framework. Being able to adjust on the fly is key to long-term success.
Resources and Budgets: Setting Realistic Expectations
HIPAA compliance isn’t free. A robust document sharing system takes investment – not just software and hardware costs, but also the time and effort needed for implementation, training, and upkeep. Don't sugarcoat it. Get your leadership on board with a realistic budget and a clear picture of the resources required. Setting clear expectations upfront will avoid headaches down the road.
Building Support: Getting Everyone On Board
HIPAA compliance isn't just an IT project; it’s an organizational culture shift. Get everyone involved, from the doctors and nurses to the admin staff. Explain why these changes are happening. Emphasize the importance of patient data protection and highlight the benefits of a secure system. When people understand the “why,” they become your biggest advocates, not your biggest obstacles.
This roadmap is your blueprint for a sustainable system. It's not about checking a box, it’s about building a culture of compliance. Ready to elevate your document creation and management while prioritizing security and privacy? Check out Whisperit, the AI-powered platform trusted by over 100 professionals.