Secure Encrypted Document Sharing Solutions | Protect Data
Why Traditional Document Sharing Is Putting You At Risk

Sharing sensitive documents is essential for daily operations in many organizations. However, relying on traditional methods like email and generic file-sharing services can expose your valuable data to significant security risks. These methods often lack robust safeguards, making them vulnerable to various threats. This isn't just a theoretical concern; it has real-world consequences.
The Dangers of Unsecured Channels
Sending a confidential document via standard email, for example, is akin to sending a postcard – anyone can potentially read it along the way. Without encryption, your data is exposed and vulnerable to interception. Hackers, malicious insiders, or even accidental disclosures can compromise your information. This can lead to data breaches, significant reputational damage, and potential legal repercussions.
Imagine sensitive client data, financial records, or valuable intellectual property falling into the wrong hands. The consequences can be devastating. Furthermore, many industries are subject to strict data protection regulations. Failing to adequately secure sensitive documents can lead to substantial fines and costly legal battles.
The rise in data breaches through unsecured channels highlights the critical need for stronger security measures. The demand for end-to-end encryption and other robust security protocols has risen sharply in recent years, driven by escalating cybersecurity threats. Over 60% of organizations have reported experiencing a data breach due to insecure file sharing in the past year.
This clearly demonstrates the importance of secure document sharing. The secure file transfer market, projected to grow from $2.35 billion** in 2024 to **$2.51 billion in 2025, reflecting a 6.8% CAGR, further emphasizes this trend. Utilizing encrypted platforms helps ensure that only authorized individuals can access shared files. For a deeper dive into these trends, see The Future of Secure File Sharing.
Real-World Risks: Beyond the Headlines
The risks of insecure document sharing extend beyond large corporations. Small and medium-sized businesses (SMBs) are equally vulnerable, often lacking the resources to recover from a significant data breach. For SMBs, the loss of client trust can be particularly damaging. This can lead to a decline in business and long-term reputational harm.
Protecting your data isn't just about implementing technology; it's about safeguarding your business and preserving the trust your clients place in you. How to Master Data Security Best Practices offers further insights into this crucial aspect of business operations. Encrypted document sharing provides the essential security layer needed to mitigate these risks and maintain the confidentiality of your sensitive information.
End-to-End Encryption: What The Experts Won't Tell You

End-to-end encryption (E2EE) is often praised as the ultimate solution for data security. But what does it actually mean for your document sharing? This section goes beyond the hype to explain E2EE and its importance in safeguarding sensitive information.
Understanding the Power of E2EE
E2EE creates a secure channel where only the sender and recipient can decrypt shared files. Even if intercepted, the data remains inaccessible to hackers. Imagine sending a sealed letter: only the person with the correct key can open and read it.
End-to-end encryption is one of the most effective methods for secure document sharing. It ensures that only the sender and recipient have access. Platforms like PreVeil offer E2EE integrated with standard email services, balancing security and usability. For more information on secure file sharing, see this helpful resource: Learn more about secure file sharing here. This robust protection makes E2EE a powerful defense against cyberattacks.
Debunking the Myths of E2EE
Some believe E2EE is complex and slows down workflows. This is a misconception. Modern encrypted document sharing solutions prioritize user experience, seamlessly integrating into existing processes. Secure collaboration is possible without sacrificing productivity.
It's important to understand the risks of traditional document sharing. Consider exploring techniques for secure sharing of documents. User-friendly design encourages adoption and empowers teams to share sensitive data confidently and efficiently.
Why Leading Organizations Are Embracing E2EE
Businesses are increasingly recognizing the shortcomings of traditional security. They are adopting E2EE for a stronger solution in the face of growing threats. Traditional methods, like password protection, are often easily bypassed.
E2EE protects the data itself, regardless of access method. This provides superior defense against unauthorized access. This added security also builds trust with clients and stakeholders.
Seamless Integration for Simple Adoption
Implementing encrypted document sharing isn't difficult. Many E2EE solutions easily integrate with current tools like email clients and cloud storage. This ensures a smooth transition without disrupting workflows.
These platforms often include features like secure key management, simplifying the process of handling encryption keys. This streamlines implementation and minimizes disruption. The easy integration makes E2EE a practical security solution for businesses of all sizes.
Battle-Tested Encrypted Sharing Platforms Compared
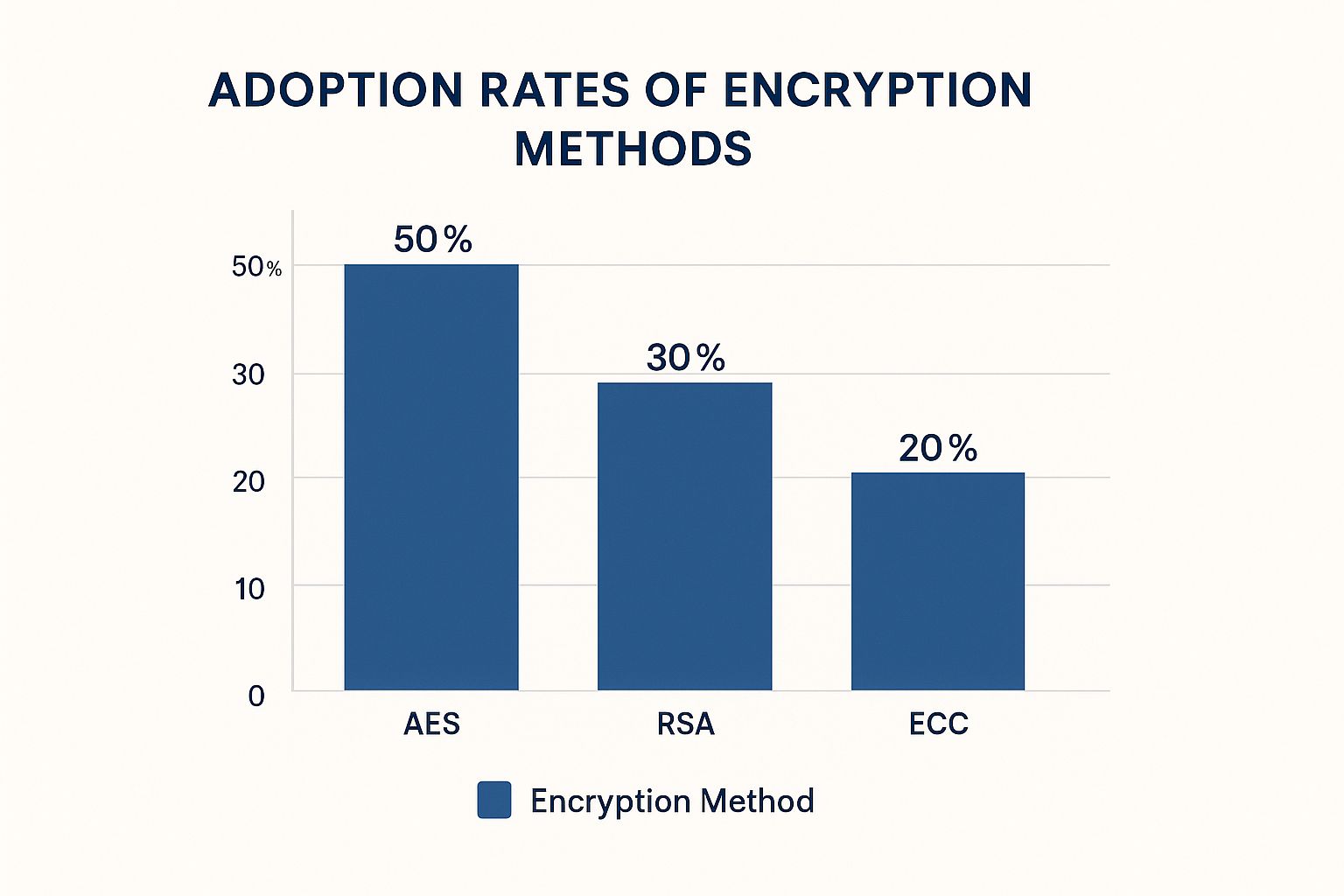
The chart above shows the current usage of different encryption methods. AES takes the lead at 50%, followed by RSA at 30%, and ECC at 20%. This clearly shows that AES is the most common standard for data encryption. However, the continued presence of RSA and the increasing use of ECC show that the world of encryption technologies is constantly changing.
Finding the right encrypted document sharing platform is a balancing act between strong security and practical use. This comparison helps you make informed decisions without the marketing hype. Several factors need to be carefully considered, including security features, usability, integrations, and pricing. You need a solution that not only protects your data but also works well with your current tools and processes. Check out our guide on improving your document security.
Key Features To Consider
Several key features play a crucial role in securing your documents. These include robust encryption methods, user authentication, and comprehensive access controls. Understanding these features is essential for choosing the best platform for your specific needs.
- End-to-End Encryption (E2EE): E2EE ensures that only the sender and recipient can read shared files, protecting them even if intercepted during transmission.
- Zero-Knowledge Encryption: With zero-knowledge encryption, even the service provider cannot decrypt and view your data, offering the highest level of confidentiality.
- Two-Factor Authentication (2FA): 2FA adds an additional layer of security by requiring a second verification method, such as a code from your phone, in addition to your password.
- Secure Key Management: Strong key management practices are essential for protecting the encryption keys that unlock your data, preventing unauthorized access.
- Access Control and Permissions: Granular access control lets you specify exactly who can view, edit, and share individual documents, ensuring data integrity.
- Audit Logs: Comprehensive audit logs track file access and sharing history, providing valuable insights for monitoring and security analysis.
- Compliance Certifications: If your organization operates in a regulated industry, look for platforms with relevant compliance certifications, such as HIPAA or GDPR.
Comparing Leading Platforms
To help you evaluate the available options, we’ve compiled a detailed comparison of popular encrypted document sharing platforms. This comparison offers a practical look at the strengths and weaknesses of each platform, focusing on key aspects like security, usability, and integrations.
To help you compare available options, we’ve created the following comparison table.
Comparison of Top Encrypted Document Sharing Platforms This table compares key features, pricing models, and security capabilities of leading encrypted document sharing solutions to help you select the best option for your needs.
| Platform | Security Features | Usability | Integration Options | Pricing Model | Best For |
|---|---|---|---|---|---|
| Hypothetical Platform A | E2EE, 2FA, Zero-Knowledge | User-friendly interface, mobile app available | Integrates with popular cloud storage | Freemium | Individuals, small teams, security-conscious users |
| Hypothetical Platform B | E2EE, Access Control, Audit Logs | Simple file sharing and collaboration tools | Limited integrations | Subscription | Businesses needing detailed access control |
| Hypothetical Platform C | 2FA, Secure Key Management | Basic interface, web-based platform | Integrates with email clients | Free | Simple file sharing with basic security needs |
| Hypothetical Platform D | E2EE, Compliance Certifications | Advanced features, complex setup | Wide range of integrations | Enterprise | Large organizations, industries with strict compliance |
This table provides a quick overview of some popular platforms. The best choice depends on your organization's specific security needs and how each platform fits into existing workflows.
Beyond The Basics: Mobile Accessibility And Collaboration
Mobile access is essential for secure document sharing in today’s fast-paced environment. Having a platform with a solid mobile app is key. This lets you access sensitive information securely, wherever you are. Seamless collaboration features, such as real-time co-editing and secure document versioning, also boost productivity without compromising security. These tools are crucial for teams working on sensitive projects that demand a high degree of collaboration. Remember, security should complement your workflow, not complicate it.
Implementing Encrypted Sharing Without Disrupting Workflow
Transitioning to encrypted document sharing doesn't have to be a complex undertaking. With a well-defined strategy, it can be a seamless process that strengthens your security without sacrificing productivity. This section outlines practical methods for implementing encrypted document sharing that your team will embrace.
Gaining Stakeholder Buy-In
The foundation of any successful implementation lies in securing buy-in from all stakeholders. Clearly articulate the advantages of encrypted sharing, emphasizing the critical role it plays in protecting sensitive data and upholding client confidentiality. For further insights, explore resources like How to Master Maintaining Client Confidentiality. Showcase how modern encryption solutions prioritize user-friendliness and integration with existing workflows. By proactively addressing potential concerns and demonstrating the long-term value of enhanced security, you can foster a smoother transition.
Conducting a Thorough Security Assessment
Prior to selecting a platform, it's crucial to assess your current security protocols and pinpoint vulnerabilities. Identify the types of documents requiring protection, define who needs access, and establish the necessary levels of control. This assessment will guide you towards a solution that aligns with your specific needs and regulatory requirements. Moreover, it will illuminate any weaknesses in your existing system, enabling proactive remediation.
Selecting the Right Solution and Integration Strategies
Choosing a platform that complements your workflow is paramount for user adoption. Prioritize solutions that seamlessly integrate with your current tools, such as email clients and cloud storage platforms. User-friendly interfaces and intuitive features are essential for minimizing the learning curve and promoting consistent usage. Seamless integration eliminates the need for cumbersome workarounds, ensuring a smooth transition and minimal disruption.
Developing Smart Access Policies and Training Strategies
Establish clear access policies that define who can access specific documents and what actions they are permitted to perform. Implement role-based access control to streamline management and ensure appropriate permissions. Comprehensive training is crucial for empowering your team with the knowledge and skills to utilize the new system effectively. Regular refresher sessions and readily available support resources can address ongoing questions and reinforce best practices.
Navigating Common Pitfalls
Many security initiatives encounter obstacles due to common implementation errors. Inadequate user training often leads to confusion and resistance. Selecting an overly complex solution can also hinder adoption and create security gaps. By anticipating and proactively addressing these challenges, you can greatly enhance the likelihood of a successful implementation. Remember, simplicity and a positive user experience are key to encouraging adoption.
Real-World Success Stories
Organizations that have successfully transitioned to encrypted sharing often highlight the value of a phased rollout. Starting with a pilot group allows you to refine your strategy and address any unforeseen issues before full deployment. These early adopters can become advocates within the organization, promoting the benefits and encouraging broader adoption. Their feedback is invaluable in tailoring the implementation strategy for the entire team. Learning from their experiences can help you avoid common pitfalls and ensure a seamless transition for everyone.
The Future of Document Security You Can't Afford To Ignore

The world of encrypted document sharing is constantly evolving. New technologies and growing security risks are changing how we protect sensitive information. Organizations must stay informed about these changes to maintain robust data protection. This section will explore the key trends shaping the future of document security.
The Rise of AI-Powered Threat Detection
Artificial intelligence (AI) is rapidly becoming essential for strong security systems. AI algorithms analyze large datasets of network traffic and user behavior, detecting unusual patterns that might indicate a breach. This proactive approach allows organizations to identify and neutralize threats before they escalate.
For example, AI can flag suspicious logins from unknown locations or identify unusually large downloads of sensitive data. This provides an early warning system against data breaches. This shift towards AI-driven security is a significant step in defending against complex cyberattacks.
Blockchain Integration for Enhanced Verification
Blockchain, the technology behind cryptocurrencies like Bitcoin, offers significant potential for securing document sharing. Blockchain creates a permanent, unalterable record of every document transaction. This ensures the authenticity and integrity of shared files.
This verification layer helps prevent unauthorized changes or tampering. Blockchain's decentralized structure also eliminates single points of failure, further enhancing security.
Zero-Trust Frameworks and the Mobile Workforce
With the increasing prevalence of remote work, zero-trust security frameworks are becoming more important. Zero trust operates on the principle of "never trust, always verify." Every user and device must be authenticated before accessing any resources, regardless of location.
This means even internal employees must continuously verify their identity, minimizing insider threats. Combining zero trust with mobile-first secure transfer solutions ensures secure access to sensitive data from anywhere, at any time. To improve efficiency, consider integrating encrypted sharing with your existing document workflow automation.
The Impact of Evolving Regulations
Data privacy regulations, such as GDPR, are constantly changing. They place increasing pressure on organizations to protect personal information. These regulations often require specific measures like encryption and data masking.
Compliance is not just a legal necessity but also vital for maintaining customer trust. Non-compliance can lead to significant fines and reputational damage. The growing interconnectedness of global businesses adds complexity, requiring adaptable and robust security solutions. For further information on data security and compliance, see this helpful resource: How to master data security and compliance.
To understand the growing importance of this area, let's look at the market projections. The secure file transfer market is expected to reach $3.63 billion by 2029, with a CAGR of 9.7%. This growth is driven by increasing cyber threats, the rise of IoT devices, and the adoption of cloud and hybrid solutions. Learn more about secure file transfer market growth here. This underscores the importance of prioritizing data security and investing in advanced solutions like encrypted document sharing.
The following table highlights some of the newest technologies impacting secure document sharing.
To help illustrate the evolving landscape, the following table summarizes some key emerging technologies and their potential impact:
Emerging Technologies in Encrypted Document Sharing
| Technology | Current Adoption Rate | Security Impact | Implementation Complexity | Expected Timeline |
|---|---|---|---|---|
| Homomorphic Encryption | Low | High (allows computation on encrypted data) | High | 5-10 years |
| Quantum-Resistant Cryptography | Emerging | High (protects against future quantum computer attacks) | Medium | 2-5 years |
| Secure Multi-Party Computation | Niche | High (enables collaborative computation on sensitive data) | High | 5-10 years |
| Confidential Computing | Growing | Medium (protects data in use) | Medium | 1-3 years |
| Blockchain-based access control | Emerging | Medium (enhances auditability and transparency) | Medium | 2-5 years |
This table provides a snapshot of the dynamic environment and how these innovations may influence security and usability in the near future. The continued adoption of technologies like blockchain integration, AI-driven threat detection, and zero-trust frameworks shows the ongoing evolution of document security.
Encrypted Document Sharing That People Actually Use
Security is only as strong as its weakest link. Often, that's not the encryption itself, but the human factor. This section explores the practical challenges of implementing encrypted document sharing that balances robust security with user-friendliness. A secure system that's too difficult to use will be abandoned or bypassed, defeating its purpose.
Key Management: The Cornerstone of Effective Encryption
Key management is fundamental to any secure encryption system. Think of it as the lock and key to your home. A strong lock is useless if the key is easily duplicated or lost. Similarly, robust encryption algorithms are worthless if the keys are mismanaged. This means protecting keys from unauthorized access while ensuring authorized users can readily access them when needed. Overly complex key management systems can frustrate users and lead to errors, potentially compromising security.
Password Policies: Balancing Security and Usability
Password policies are another crucial element. Strong, complex passwords are essential, but overly stringent requirements can lead to poor password practices. Requiring excessively long passwords with multiple special characters can encourage users to write them down or reuse them across accounts, weakening overall security. A practical approach balances password strength with memorability, perhaps incorporating tools like password managers for secure storage and retrieval.
Document Classification: Applying Appropriate Protection Levels
Not all documents need the same level of protection. Document classification categorizes documents based on sensitivity, allowing for appropriate security measures. Highly confidential information, like financial records or personal data, requires the highest level of encryption. Less sensitive documents can have less stringent measures. This tiered approach allocates resources effectively and avoids burdening users with unnecessary protocols for less sensitive information. For further information on document management, see this article on legal document automation software.
Audit Logging: Detecting Suspicious Activities Without Overwhelm
Audit logs record who accessed which documents and when, providing valuable insights for monitoring and security analysis. However, excessive log data can obscure real threats. Effective audit logging establishes clear criteria for suspicious activity and implements automated alerts for those events. This focused approach allows security teams to respond quickly to potential breaches without being overwhelmed by routine activity.
Document Lifecycle Management: Protection From Creation to Disposal
Security extends beyond the initial sharing of a document. Document lifecycle management encompasses a document's entire lifespan, from creation to disposal. This includes protection during storage, transit, and collaboration, along with secure disposal procedures to prevent data recovery from discarded documents. A comprehensive lifecycle approach ensures continuous protection and minimizes breach risks.
Ready to experience secure and efficient document management? Visit Whisperit to learn how their AI-powered platform can transform your workflow while prioritizing the privacy and security of your sensitive information.