Your Guide to Data Processing Agreement Templates
A Data Processing Agreement, or DPA, is the legally binding contract that spells out exactly how a third-party vendor is allowed to handle the personal data you've collected from your customers. This isn't just a friendly handshake or a suggestion. For any business that falls under regulations like GDPR, it's a mandatory document. It’s the formal agreement that defines the rules of the road between you and your partners.
Why You Can't Afford to Ignore DPAs

Take a moment to think about all the external services that touch your customer data. Your cloud hosting provider, the marketing automation platform you rely on, even your analytics tools—they all count.
In the eyes of the law, you are the data controller. You're the one deciding why and how that personal data gets processed. Your vendor? They are the data processor, and they’re only supposed to act on your specific instructions.
This controller/processor distinction is absolutely critical. You, as the controller, are ultimately on the hook for protecting that data, even when it's sitting on a third party's servers. A DPA is the legal tool that makes your processor accountable, ensuring they uphold the same high data protection standards you do. Without one, you’re flying blind and leaving a massive gap in your compliance strategy.
The Real-World Risks of Not Having a DPA
Let’s get practical. Imagine your SaaS business uses an outside service to handle customer support tickets. That service holds customer names, email addresses, and potentially sensitive conversation histories. If that vendor gets hit with a data breach and you don't have a solid DPA in place, guess who regulators come after? You. The legal and financial fallout lands directly on your company.
These aren't just hypothetical scenarios. Since GDPR came into force, European authorities have been flooded with nearly 65,000 data breach notifications. The fines for non-compliance are steep, with penalties for things like inadequate DPAs climbing as high as €10 million or 2% of a company's global annual turnover—whichever is higher.
To give you a clearer picture, here's a quick rundown of what every solid DPA should contain.
Key DPA Elements at a Glance
| Clause | What It Defines | Why It's Critical |
|---|---|---|
| Parties & Roles | Clearly identifies the Data Controller (you) and the Data Processor (your vendor). | Establishes the legal relationship and responsibilities from the outset. |
| Subject Matter | Describes the type of data, categories of data subjects, and the duration of processing. | Provides specific context and scope, preventing ambiguity. |
| Processor's Obligations | Spells out that the processor must only act on the controller's documented instructions. | This is the core of the agreement, ensuring you maintain control over the data. |
| Security Measures | Details the technical and organizational security measures the processor must implement. | Guarantees that the vendor meets required security standards to protect the data. |
| Sub-processors | Outlines the rules for engaging other vendors (sub-processors) to process the data. | Prevents your data from being passed along to other parties without your knowledge or consent. |
| Data Breach Protocol | Defines the process for notifying the controller in the event of a data breach. | Ensures timely communication so you can meet your own breach notification obligations. |
This table just scratches the surface, but it highlights the non-negotiable components that form the backbone of a compliant agreement.
A common misconception is that a DPA is just a checkbox formality. It's not. It’s a foundational piece of your entire data governance and risk management strategy, defining liability and security expectations before something goes wrong.
A well-crafted DPA is an essential part of any robust cyber security risk management program. It's about more than just avoiding fines; it’s about building genuine trust with your customers by showing you take protecting their information seriously. This is especially true in heavily regulated sectors, a topic we explore further in our HIPAA compliance requirements checklist. Starting with a solid data processing agreement template is your best first line of defense.
Taking the DPA Template Apart, Piece by Piece
Staring at a data processing agreement can feel like looking at a wall of dense legalese. It's easy to feel overwhelmed. So, let's break it down into manageable pieces, explaining what each clause actually means for your business and why you can't afford to skip any of them. This isn't just a box-ticking exercise; it's about understanding the promises you're making and the protections you're getting.
A good way to think about your DPA is as a very specific instruction manual for your vendor. If the instructions are fuzzy, mistakes will happen. But clear, written instructions—which is exactly what Article 28 of the GDPR demands—mean your data gets handled the way you, and the law, expect.
Subject Matter and Duration of Processing
This first part really sets the scene for the whole agreement. It has to be incredibly clear about what data is involved, who it belongs to, and how long the vendor will be handling it. You want to avoid generic descriptions at all costs; they're a major red flag.
Let’s say you’re bringing on a new marketing analytics tool. A well-drafted clause would look something like this:
- Subject Matter: The processing of our user engagement data.
- Nature and Purpose: To analyze website traffic, track user behavior for product improvement, and generate performance reports for our internal teams.
- Categories of Data Subjects: Our website visitors and registered platform users.
- Types of Personal Data: IP addresses, cookie identifiers, page-view history, and user account IDs.
- Duration: For the length of our main service contract.
If this section just says something like "customer data" for "business purposes," you're leaving a massive grey area that could cause you headaches down the line.
Processor Obligations and Your Instructions
This is the real heart of the DPA. It's where you put it in writing that the processor can only act on your documented instructions. This simple sentence is a powerful legal tool that ties them to your rules and prevents them from going rogue with your data. It stops a vendor from, say, using your customer list to train their new AI model or selling aggregated data insights without you ever knowing.
I see a lot of businesses overlook this, but it's a critical point: without this clause, you effectively lose control the second that data is out of your hands. The DPA is what legally reasserts your role as the data controller and makes that vendor an extension of your own compliance efforts.
Keeping track of these agreements and ensuring the instructions are always up-to-date is a big part of running a tight ship. For smaller businesses, having a solid system for document management for small business is the perfect foundation for handling DPAs and other essential contracts.
Security of Processing and Technical Measures
Alright, now we're moving from legal promises to the practical, technical stuff. A weak DPA will often just have a vague line about the processor "keeping the data secure." That's not good enough. A strong DPA demands specifics.
This is the place to spell out your non-negotiable security requirements. I always recommend including things like:
- Encryption: Insist on encryption for data both in transit (like TLS 1.2 or higher) and at rest (using a strong standard like AES-256).
- Access Controls: Make sure data access is restricted to authorized staff on a strict need-to-know basis, protected by multi-factor authentication.
- Audits and Certifications: You should have the right to audit their security measures or, more practically, require them to maintain respected certifications like ISO 27001 or SOC 2.
Don't ever feel hesitant about asking for these details. If a potential vendor pushes back or can't commit to basic security standards in writing, that's a tell-tale sign you should walk away. Your customers' data is on the line, and it deserves protection you can actually verify.
How to Customize Your DPA for Any Vendor

A good data processing agreement template is a fantastic starting point, but it's never the finish line. Every vendor relationship you have is unique, and your DPA has to reflect that reality if you want real legal protection. Treating it like a one-size-fits-all document is a classic mistake—and one that can leave your company dangerously exposed.
The real skill lies in adapting the core clauses of your template to the specific situation. The type of data you're sharing, the service the vendor is providing, and the risks involved will all change which parts of the DPA need the most attention.
Let's walk through a few real-world examples.
Tailoring for a B2B Software Integration
Imagine you’re integrating a new Customer Relationship Management (CRM) platform into your B2B software stack. This isn’t just any tool; it will be handling a massive amount of customer data—names, contact details, sales conversations, you name it. In this scenario, your top priorities are control and specificity.
When you sit down to customize the DPA, you need to sharpen your focus on these key areas:
- Nature and Purpose of Processing: Get granular. Don’t just say "managing customer data." Instead, spell it out: "storing customer contact information, tracking sales pipeline activity, and logging customer support interactions for the sole purpose of providing CRM services." Precision is your friend here.
- Sub-processors: Most CRM providers don't go it alone; they rely on other cloud services for their infrastructure. You have every right to demand a complete list of their sub-processors and, crucially, the right to approve any new ones they want to bring on board.
- Data Deletion: What happens when you eventually switch CRMs? Your DPA needs a rock-solid clause that forces the vendor to completely and verifiably delete all your customer data from their systems within a set timeframe, like 30 days after the contract ends.
This level of detail isn't just about ticking boxes. It ensures the CRM provider knows exactly where the boundaries are and gives you clear contractual grounds to enforce them if something goes wrong.
Heightening Security for a Health-Tech Startup
Now, let's raise the stakes. Say you're a health-tech startup using a cloud service to process patient health information (PHI). The risk profile here is exponentially higher, and your DPA has to be just as robust. Standard security clauses won’t even come close to cutting it.
Your job is to customize that DPA to build a digital fortress around the data.
- Stricter Security Measures: Move past generic promises. Mandate specific security protocols, such as end-to-end encryption for all data at rest and in transit, strict role-based access controls, and a commitment to regular penetration testing.
- Breach Notification Timeline: When you're dealing with sensitive health data, you can't afford to wait. Your DPA should slash the notification window from the standard "without undue delay" to a fixed, aggressive period, like within 24 hours of discovery.
- Audit Rights: Don't just take their word for it. Insist on the contractual right to conduct your own security audits or demand recent compliance reports (like a SOC 2 Type II or HIPAA attestation) to verify their security posture.
For high-risk data, the DPA transforms from a compliance document into a critical risk mitigation tool. Every clause should be scrutinized through the lens of "what's the worst that could happen?" and fortified accordingly.
This proactive approach is a cornerstone of building a comprehensive data privacy compliance framework that can actually stand up to regulatory scrutiny.
Defining Logistics for an Online Retailer
For our last scenario, let's consider an online retailer bringing on a third-party logistics (3PL) partner to handle warehousing and shipping. The personal data involved includes customer names, addresses, and order details. Here, the risk isn't just a data breach but also operational headaches and data inaccuracy.
For a 3PL partner, your DPA customization should be all about clear boundaries and logistics:
- Data Minimization: Make it crystal clear that the 3PL can only access the data absolutely necessary for fulfilling orders—and nothing more. No marketing, no analytics, just shipping.
- International Transfers: If your 3PL partner operates globally, the DPA must specify the legal mechanisms governing any cross-border data transfers, such as the EU's Standard Contractual Clauses (SCCs).
- Data Return: At the end of the partnership, what happens to all that data? The DPA must outline a secure process for how order histories and customer addresses will be returned to you.
The sheer complexity of managing these agreements is fueling a massive investment in compliance tech. The global data privacy software market is projected to explode from USD 5.37 billion in 2025 to USD 45.13 billion by 2032. This isn't just a niche industry; it's a sign that getting your DPA right is no longer just a legal task—it’s a fundamental business function.
Navigating International Data Transfer Rules
Things get a lot more complicated when your data starts crossing borders. This is a huge deal if you’re moving personal data out of the European Union or the UK into a country that doesn't have an "adequacy decision"—think places like the United States. In these cases, your standard DPA isn't enough on its own. You need an extra layer of legal protection to make the transfer lawful.
For a long time, the most reliable tool for the job has been Standard Contractual Clauses (SCCs). These are essentially pre-approved contract templates issued by the European Commission. Both parties—the data exporter and the importer—sign them, creating a legally binding commitment for the importer to uphold EU-level data protection standards, no matter where they are. It’s like a legal guarantee that the data’s protection travels with it.
UK Specifics and Added Diligence
After Brexit, the UK created its own mechanism, the International Data Transfer Agreement (IDTA), which does the same job for data leaving the UK. But here’s the crucial part: whether you're using EU SCCs or the UK's IDTA, you can't just sign and forget. You now have to conduct a Transfer Impact Assessment (TIA).
A TIA is basically a due diligence exercise. You have to actively investigate whether the laws in the recipient's country could interfere with the promises made in the SCCs or IDTA. For instance, could government surveillance programs in that country allow authorities to access the data in a way that GDPR would never permit? This has become a non-negotiable step before you onboard any new processor outside the EU/UK.
You can't just sign the SCCs and assume you're compliant. The TIA forces you to actively assess and document the real-world risks to the data you're transferring. It’s a mandatory step that proves you’ve done your homework.
The image below points out some of the key security metrics that always come under the microscope during these kinds of assessments.
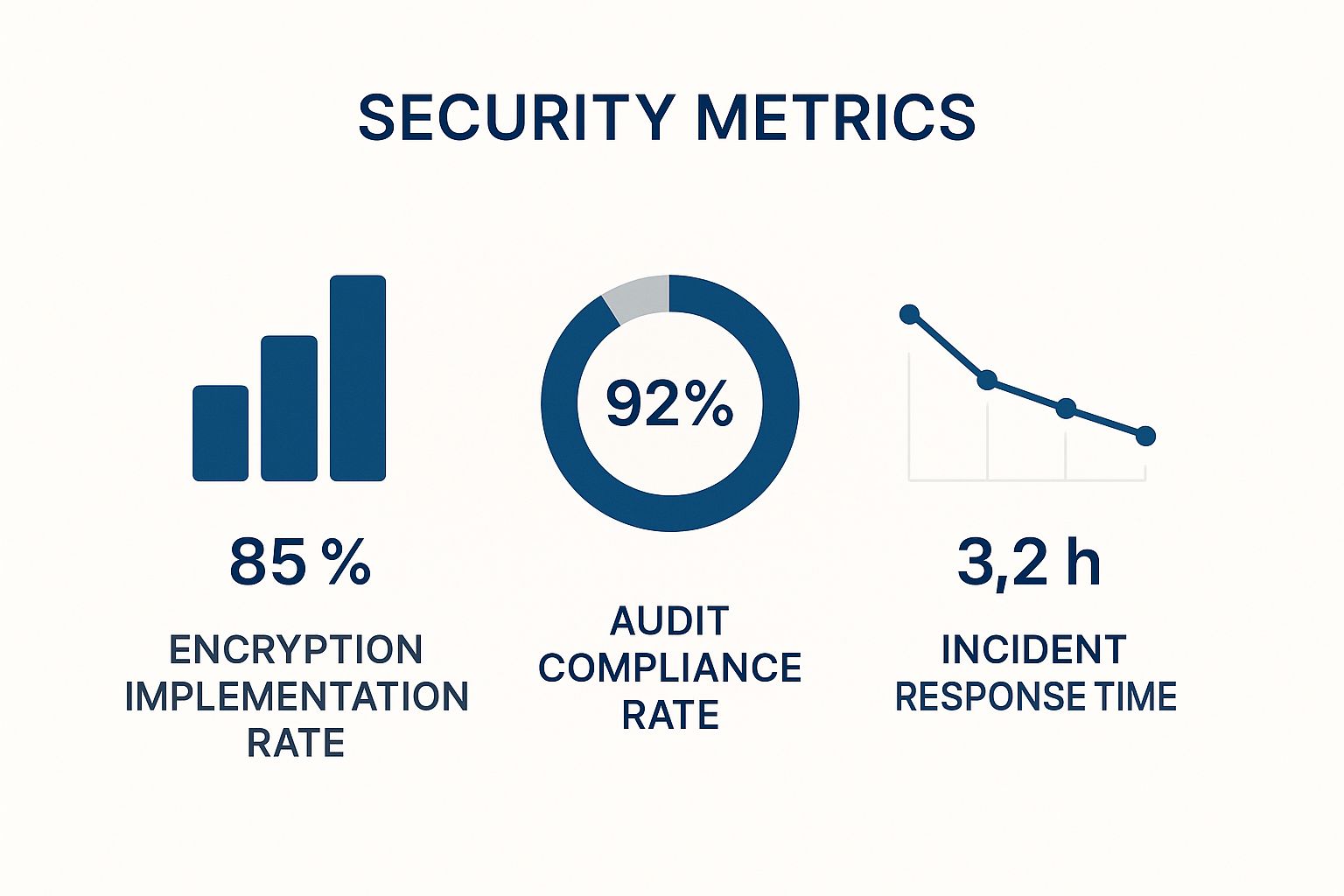
These numbers aren't just for show; they offer concrete evidence that a processor is serious about security, which is a massive part of a successful TIA.
The need for this specialized compliance work has created a booming industry. In fact, the global market for GDPR services—which includes drafting and managing these very agreements—was valued at USD 3.0 billion in 2024. Projections show it rocketing to USD 16.8 billion by 2033, which gives you a sense of just how critical this has become for businesses everywhere.
To help you get a clearer picture of your options, here’s a quick comparison of the most common transfer mechanisms.
International Data Transfer Mechanisms Compared
| Mechanism | Best For | Key Requirement |
|---|---|---|
| Adequacy Decisions | Transfers to pre-approved countries (e.g., Japan, Canada). | The European Commission has already deemed the country's data protection laws as "adequate." |
| Standard Contractual Clauses (SCCs) | Transfers to most non-adequate countries, including the US. | Must be supplemented with a Transfer Impact Assessment (TIA) to verify protections. |
| Binding Corporate Rules (BCRs) | Large multinational corporations transferring data between their own entities. | Requires a lengthy and complex approval process from a data protection authority. |
Each of these has its place, but for most businesses working with third-party vendors, SCCs combined with a solid TIA will be the path you’ll take.
Ultimately, conducting a TIA is a vital component of a broader third-party risk assessment. The whole point is to make sure your international data flows are built on a legal foundation that will stand up to scrutiny.
Common DPA Mistakes That Leave You Exposed
Just having a signed Data Processing Agreement doesn't automatically mean you're compliant. I’ve seen it time and time again: a business signs a vendor's DPA or grabs a generic template off the internet, thinking they've ticked the GDPR box. But the truth is, the devil is always in the details.
These aren't just minor oversights. They are fundamental gaps that can make your DPA practically worthless, giving you a false sense of security while leaving your company wide open to massive fines and reputational damage. An agreement full of holes is almost as bad as having no DPA at all.
Using Vague or Overly Broad Language
The most common—and most dangerous—mistake I see is vague language. This is especially true when it comes to defining the scope of data processing. A clause stating the processor will handle "customer data for business purposes" is a huge red flag. This kind of ambiguity gives the vendor far too much freedom and fails to meet GDPR's strict requirement for specificity.
Let's walk through a real-world example of how to tighten this up.
- Before (Vague): "The processor will process personal data to provide the contracted services."
- After (Specific): "The processor will process user email addresses and purchase histories for the sole purpose of sending transactional email notifications and generating monthly sales reports for the controller."
See the difference? The second version creates clear, enforceable boundaries. It leaves no room for creative interpretation by defining exactly what data is being processed and why. This is precisely what regulators are looking for.
A DPA's strength lies in its precision. If you can't tell exactly what a vendor is supposed to be doing with your data just by reading the agreement, then the document isn't doing its job.
Overlooking Data Return and Deletion Protocols
So, what happens to your data when the contract with a vendor ends? It’s a critical question that many DPAs simply fail to answer. Forgetting to include a solid clause for the return or deletion of data is like leaving the back door of your house unlocked after you've moved out.
You need to spell out a clear, time-bound process. The clause should require the processor, at your discretion, to either securely return all personal data or permanently wipe it from their systems—and that includes backups. It's crucial to set a firm deadline, like within 30 days of contract termination.
Properly managing the lifecycle of these documents is a core part of compliance, which is why following strong document management best practices is non-negotiable.
Neglecting Breach Notification Requirements
Another gaping hole I often find is a weak or completely missing data breach notification clause. Sure, GDPR says processors must notify controllers "without undue delay," but relying on that vague phrase is a rookie mistake.
Your DPA needs to set a much stricter timeline. For example, you can—and should—require notification within 48 hours of discovery. Why so tight? Because you often only have 72 hours to report the breach to the authorities. That extra 24 hours gives your team precious time to investigate and prepare, turning a potential crisis into a managed response.
Frequently Asked Questions About DPAs

Even with a great template in hand, you’re bound to have some practical questions. Let's tackle the most common ones I hear, so you can move forward with confidence.
DPA vs Privacy Policy: What Is the Difference?
This is a classic point of confusion, but the distinction is actually quite simple.
Think of your Privacy Policy as a public-facing promise. It’s the document on your website that tells your customers, "Here’s what personal data we collect from you, why we collect it, and what we do with it." It's all about transparency with the people whose data you're collecting directly.
A Data Processing Agreement (DPA), on the other hand, is a behind-the-scenes, legally binding contract. It's between you (the data controller) and another company that processes data for you (the data processor), like your email marketing provider or cloud storage service. The DPA lays down the law on how they must handle your data.
So, one is a public promise, and the other is a private contract. You absolutely need both for solid compliance.
How Often Should a DPA Be Reviewed?
A DPA is never a "set it and forget it" document. In my experience, the best approach is to schedule a review at least once a year. You should also pull it out any time there’s a significant change in your relationship with the processor.
Key triggers that should have you immediately dusting off that DPA include:
- New Services: Your vendor is now offering a new feature or service that changes the scope of data processing.
- New Sub-processors: They've hired another company (a sub-processor) to help them, and that company will now have access to your data.
- Legal Updates: Data protection laws evolve. A major update, like the introduction of new Standard Contractual Clauses (SCCs), means your DPA needs a refresh to stay compliant.
Don't just file your DPAs away and forget about them. Active, regular reviews are a hallmark of a mature compliance program. They ensure the agreement actually reflects how data is being handled today, not just a year ago, protecting you from new risks as your business relationships evolve.
What Happens if a Processor Violates the DPA?
This is where a well-drafted DPA really proves its worth. If a processor messes up and breaches the terms of the agreement, you aren't left scrambling. The DPA should give you a clear playbook for what to do next.
First, it should detail your right to terminate the contract. It should also specify that you can require the processor to securely return all your data or delete it permanently.
More importantly, the DPA establishes the processor's liability. Let's say their negligence leads to a data breach, and you're hit with a massive fine from regulators. The DPA provides the legal foundation for you to hold the processor accountable and seek reimbursement for the damages their actions caused. It’s your contractual shield.
Ready to create secure, compliant documents faster than ever? Whisperit uses advanced AI for dictation and editing, all within a GDPR and SOC 2 compliant framework. See how professionals are transforming their workflows by visiting the Whisperit website.